The Tor network is borne out of a research project by the Naval Research Laboratory and Defence Advanced Research Projects Agency called Onion Routing.
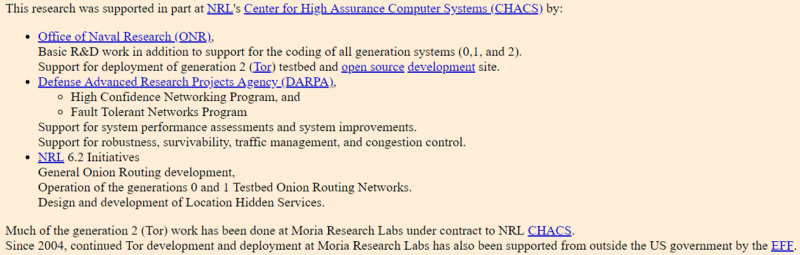

The second generation of this research is referred to as ‘the onion routing’ network. The way in which this network functions is to have layered encryption and routing via a route of entry, relay and exit nodes as is visible diagrammatically below.

This network architecture enables anonymity and privacy. Whilst this can be used in order to facilitate communication in hostile environments and enable dissidents and political activists to communicate securely; there are other use cases. Additionally Facebook and some other legitimate sites have a Tor presence.
Some of the main practical use cases of the Tor network are to enable anonymous communication between cybercriminals, the drug trade, financial fraudsters and paedophiles. Whilst these different variants of crime exist on the Tor network, a variant of crime from which valuable information can be extracted from is cybercrime.

Search Engines
Although one of the dark web’s defining features is that it is not as easily compiled by search engines as it’s clearnet equivalent, there exist a number of search engines within the darkweb. At the time of writing there are three particularly prominent darknet search engines, although others exist:
- Ahmia
- NotEvil
- Torch
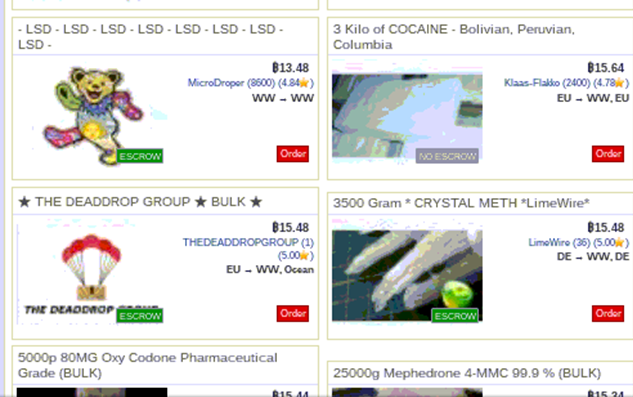
Cybercrime Market
The cybercriminal ecosystem has matured into a massive growth industry. The complexity of this ecosystem is illustrated in the following diagram from the paper ‘Drops for Stuff: An Analysis of Reshipping Mule Scams‘, which offers an analysis of the complexity of modern cybercriminal networks. Reshipping mules are an effective way for cybercriminals to cash out credit cards that have been illegally acquired.
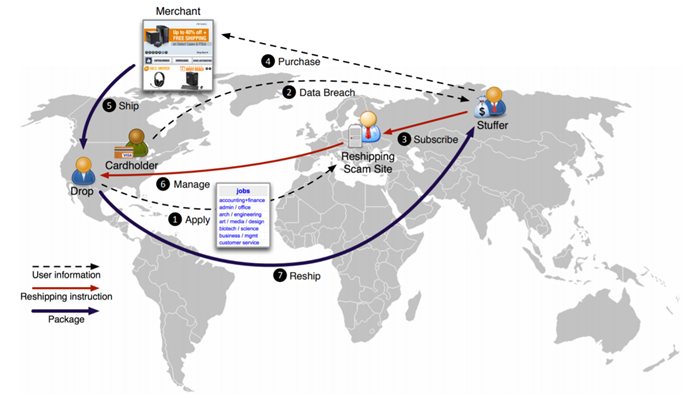

The way in which this ecosystem works is that cybercriminals attempting to ‘cash out’, carder parlance for turning stolen credit card details into money, will recruit unsuspecting mules. This recruitment is through adverts where people unlikely to gain employment in other sectors can earn a lot of money through allegedly legitimate work as a reshipper, as seen in the advert below. They then order goods to these mules location using the stolen card details, without triggering the credit card company’s location-based anti-fraud algorithms and get them to reship to a PO box in the credit card fraudster’s country of origin. Frequently these mules do not get paid, but the fraudster does, once they have sold the reshipped goods.
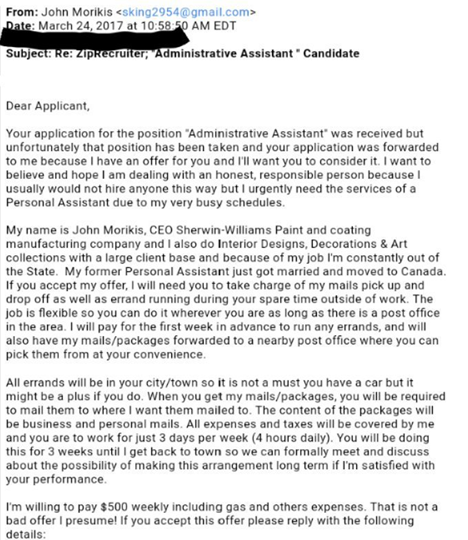

The maturity of this cybercriminal marketplace means that there are a number of competing sellers for each stage of the acquisition and laundering process. There are also medical records for sale for a large amount of money per record. Fullz, as the name would suggest, are identity records that contain full information for a given person:
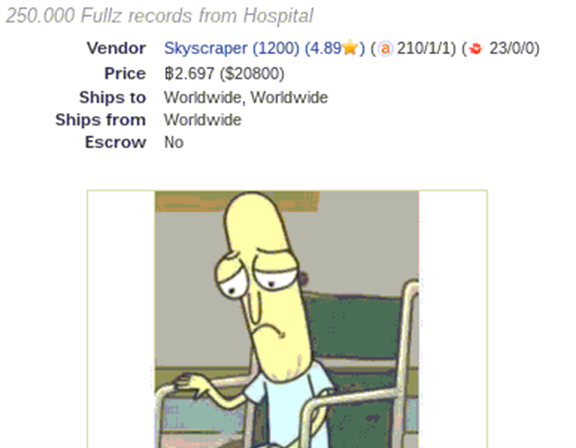

Also, with a touch of the macabre, the same vendor is also offering children’s medical records. These medical records are valuable as it allows people to open accounts in the name of these children. By the time the children need to utilise the credit or banking system and become aware of the identity theft, their credit scores may be ruined.

It appears that the customers for these records are satisfied with their purchases as judging by the product ratings, a system inspired by legitimate e-commerce sites.

However the main business of these forums is to enable the perpetration of credit card fraud and other such financial crime as well as to enable the flow of drugs outside the bounds of the law. The sophistication of some of the specialist carding stores is advanced, with specialist branding, such as the Brian Krebs Carding Store and 21 Dump Street.


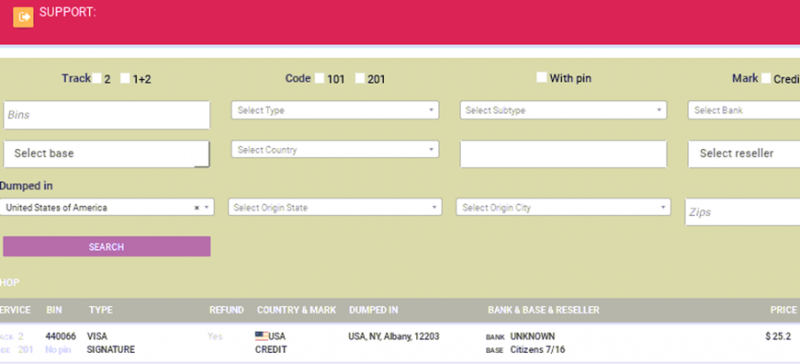
The amount of localisation and customisation offered by some of these sites mimics that of legitimate e-commerce stores, offering subdivision by bank, pin, freshness and other variables. This is due to the fact that the cybercriminal ecosystem for this data is advanced to the degree that good customer service enables a brand to differentiate itself from the competition.

Cybercrime Forums
A way in which cybercriminals operate and communicate is through the use of web forums. These are exactly the same as forums in the clearnet, except the subject matter is a little different. Just as darknet markets are somewhat of a Doppelgänger of their legitimate incarnations on the regular internet, cybercrime forums imitate the structure and manner of communication of legitimate forums.
On these cybercrime forums there are frequently links to data breaches, sales of stolen data and other trading of illicit digital goods. This is often based on a reputation system similar to the marketplaces, wherein the more transactions a vendor has conducted where the counterparty has not been duped, the more trustworthy he is deemed to be by the other elements of the criminal fraternity.
However it makes sense to be cautious when using these forums to find data leaks or similar, as many files have been trojanised. In this instance, a forum user has warned that a given leak is trojanised with dropper malware. However this altruism is anomalous within the cybercriminal underworld.
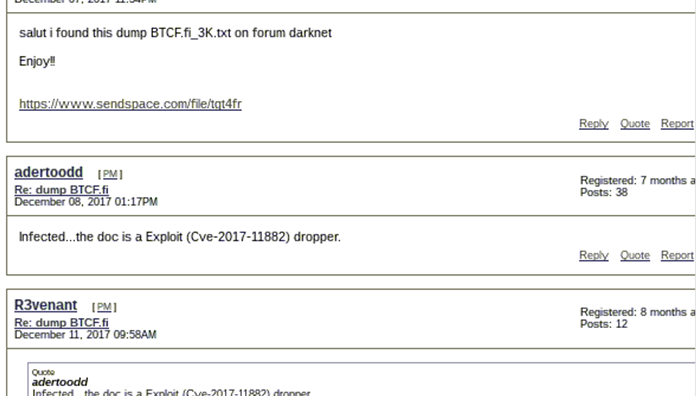

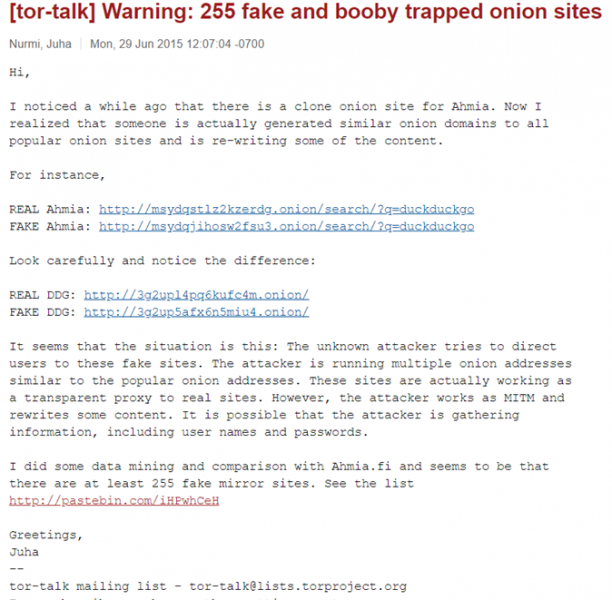
Additionally many sites operate solely to extract details from visitors to the site, there are also fakes of legitimately illegitimate sites, designed to try and dupe people for credentials as shown by the following research on the Tor mailing list.

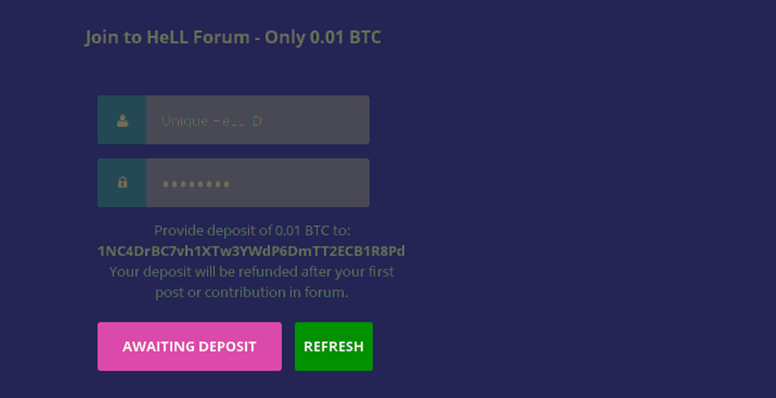
Some forums that are in the cybercrime underground offer a more restrictive entrance policy, designed to ward off security researchers, cybercrime journalists and law enforcement. These restrictive entrance policies will take the form of things such as entrance fees and also required recommendations or references in order to gain entrance.


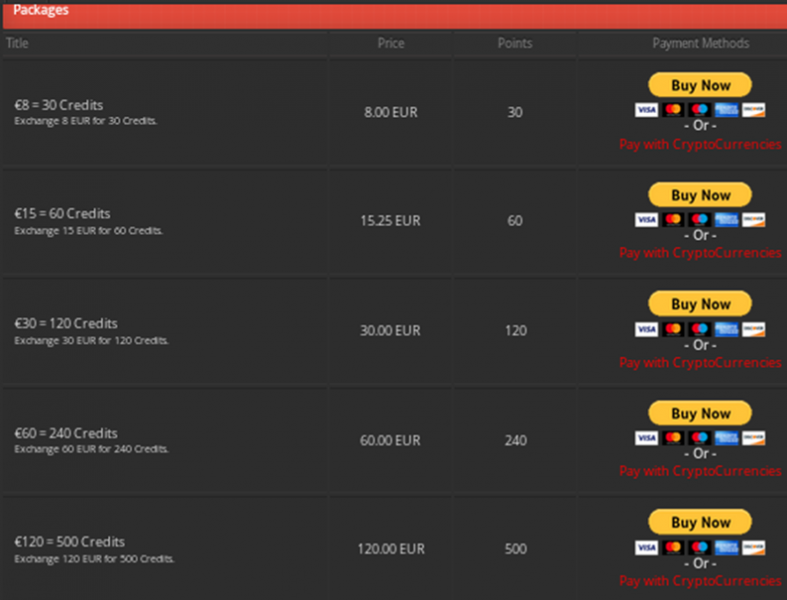
This mirrors the practices operated by more well-established leak sites on the clearnet such as RaidForums, which requires the purchase of credits in order to gain access to credentials from data breaches.

Automated Scraping
OSINT via automated scraping of the site is possible through tools such as Onionscan, which allow a wide breadth of sites to be connected to and have data and metadata pulled. It is also possible to manually write scanners, which connect to, aggregate and process a large number of dark web domains.
Analysis
In order to process gathered data dumps into something meaningful, once you have downloaded a few credential lists it is necessary to assess the relevance and timeliness of these leaks. This is in many ways one of the most difficult parts of the gathering of leaks relevant to a given organisation. It is difficult to ascertain which parts of the dump are still useful without testing the credentials.
This is possible to an extent by cross-referencing the leak with other known leaks. One useful way which this can be done is by comparing with Troy Hunt’s haveibeenpwned database, which allows individual and also rate limited queries, that allow you to decorate discovered email addresses with additional information, notably potential breach date. This allows the establishment of some degree of provenance.
Conclusion
It is possible to conclude that there are a wide range of activities being conducted on the Tor network. The anonymity of the network also facilitates the conduction of criminal activity. It is possible to extract meaningful information and threat intelligence from sites contained on the Tor network.
