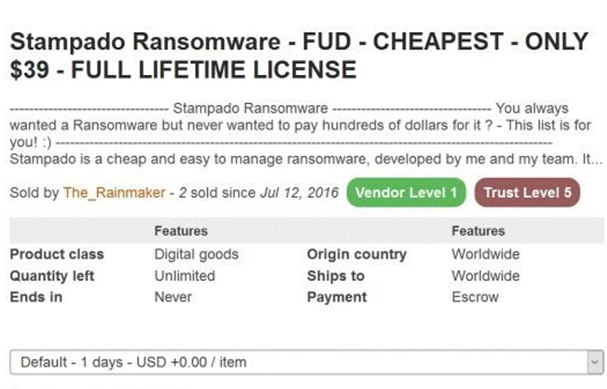
Some of the forensic countermeasures used by malware authors are described within this blog post. The importance of remaining undetected has led to the continuation of the practice of malware authors advertising their product as Fully UnDetectable (FUD). The following advert is from a cybercriminal marketplace, where ransomware is on sale, this variant, Stampado, being advertised as Fully UnDetectable.

The size of the malware corpus is growing exponentially, with the barrier to entry lowering due to openly available toolkits, such as RIG EK and Necurs, allowing for redistribution of variants of similar malware. There are also open source and user-friendly tools that allow for the creation of polymorphic malware to evade static and heuristic analysis. The most popular malware variants for cybercriminals have recently shifted from Ransomware, such as Cerber, NotPetya and Wannacryptor, to cryptomining malware, such as Adylkuzz, JenkinsMiner, Wannamine and banking trojans like Emotet and Gh0st.
The increased prominence of malware, such as banking trojans and cryptojackers, for which a lack of publicity, detection or analysis presents a strategic marketplace advantage, has increased the importance and complexity of measures to evade forensic analysis, through the use of anti-forensic countermeasures.
Anti-VM
One of the most common mechanisms that malware uses to evade forensic analysis, is remaining inert or removing itself when it detects that it has been executed from within a virtualised environment. This is to prevent automated analysis, detection and signature submission by antivirus software or malware analysts.
The ability for malware to accomplish this task is accomplished through two main methods. Firstly, malware will attempt to ascertain the validity of the physical characteristics of its surrounding environment, and secondly, malware will attempt to assess the validity of the other programs running and whether they can be determined to be analysis or virtualisation tools.
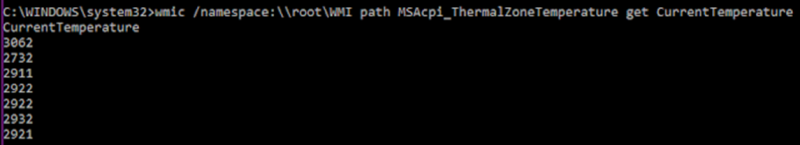
This validation of the physical environment is accomplished through assessing the amount of storage, amount of RAM, and the processing power that is available. Or, in the innovative case of GravityRAT, the temperature of the machine, as shown below.

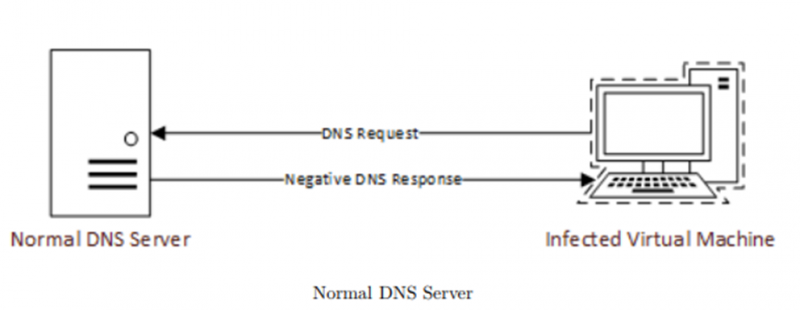
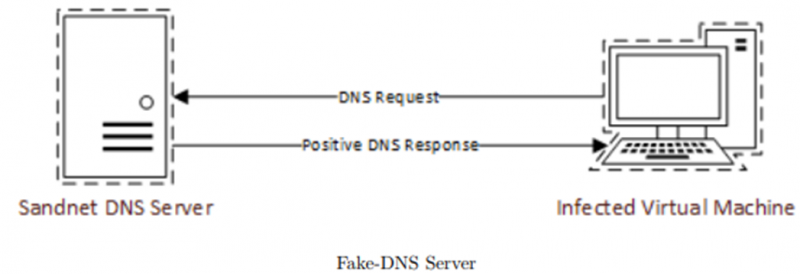
Additionally, the networking setup of the system on which the machine is executing will be analysed to detect whether or not the machine is executing in an analysis environment. There may be the use of killswitches, such as that in Wannacryptor, that poll non-existent domains to check whether they are executing in a sandnet, such as that enabled by FakeDNS. FakeDNS would return a positive result, whereas a normal DNS server would return a negative one.


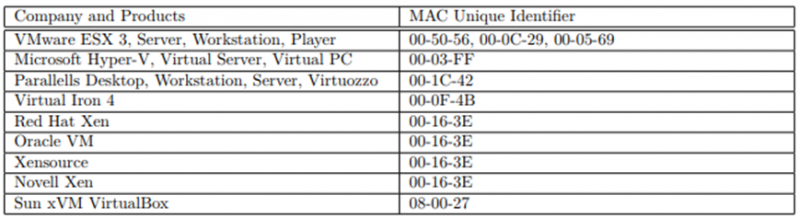
However, despite the infamy of the ‘killswitch’ domain used by Wannacryptor, a far more common method used by malware to discover whether or not it is executing in a virtualised environment is by checking the MAC addresses of the local network interfaces, to see whether they match known virtualisation platform signatures:

There are also behavioural indicators of liveness within a system. These are things such as activity within the registry, browser caches, total amount of cookies, and system events. Additionally, malware in the wild will often also look for signatures indicative of installed common analysis tools, such as IDA pro and Python.
Anti-Anti-Forensics
As a result of this, malware analysts will use tools in order to spoof the signatures resultant from the execution of malware, so that they are able to bypass anti-forensics countermeasures implemented by malware authors. There are tools, such as Paranoidfish, that show indicators of a virtual machine, so that an analyst can remove these, to better simulate a virtualised environment.
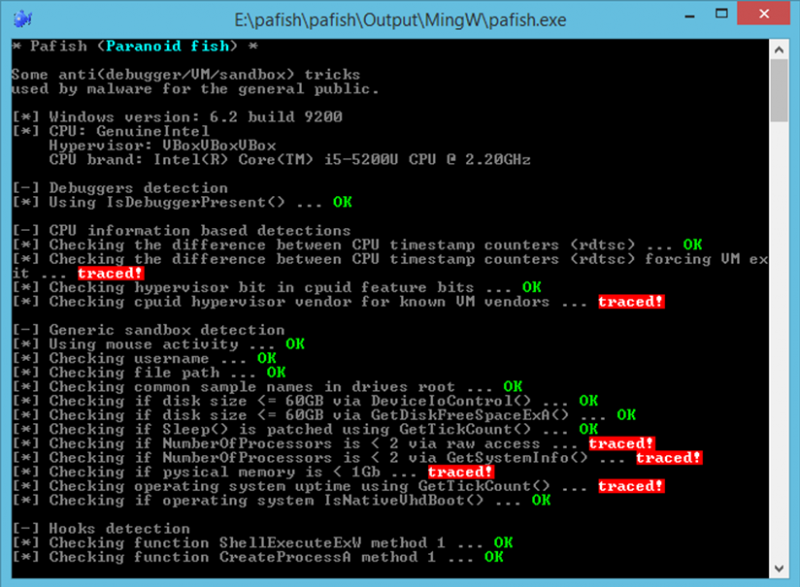

However, for the purpose of malware forensics, the most effective method of bypassing these anti-forensics capabilities is to simply install an operating system on the hardware itself. Antivirus companies frequently have air-gapped bare metal infrastructure provisioned for this reason.
Packers
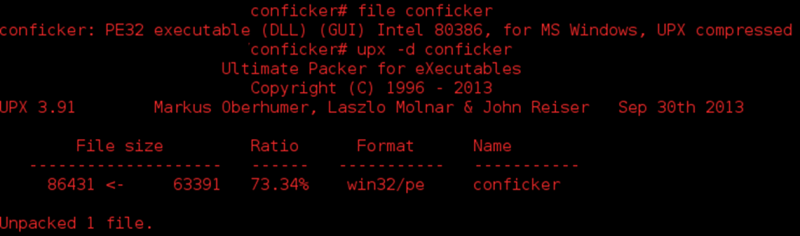
Packers are a common method of obfuscating the physical signature produced by a given malware. There are a number of free and open source packers available, such as Ultimate Packer for eXecutables (UPX), Mpress and PECompact. There are also closed source packers used within the cybercriminal community. Both packer types, though most often closed source, are frequently used by malware authors in order to evade signature-based antivirus systems and obfuscate analysis by encrypting the malware’s payload (cryptors). The following image is an example of malware packed using UPX which shows that this is a technique used in the wild:

Rootkits and Bootkits:
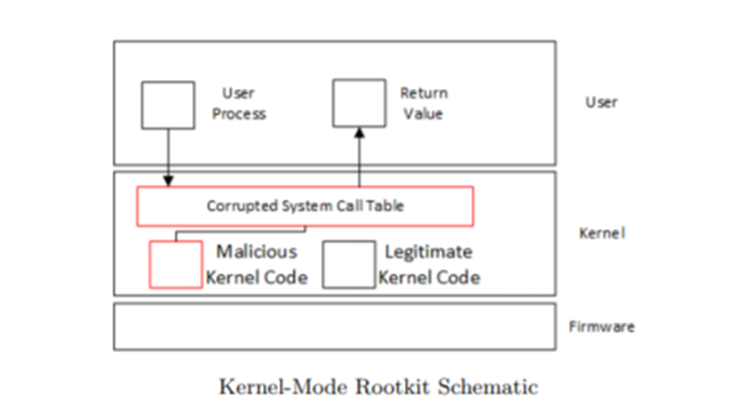
Rootkits aim to provide and maintain persistence on an infected system. They are a malware variant, whose goal is to gain the highest level of privilege escalation that they can, via corruption of the kernel for a given operating system. As such, rootkits often remain undetected by signature-based analysis. Bootkits are a particularly pernicious form of rootkits, which aim to corrupt the master boot record or volume boot record.

Network Forensics
With the increase in heuristic and behavioural analysis, and security operations centres, there is a parallel rise in the amount of scrutiny being given to the network traffic of executables. To this end, there have been attempts to obfuscate the command and control traffic necessary for the operation of many malware types.
Obfuscation – Hiding in Plain Sight
As enumerated in the 2015 BlackHat talk, ‘Hiding in Plain Sight Advances in Malware Covert Communication Channels‘, DNS Requests can also be used for covert exfiltration and command and control communication. The idea of this being that there won’t be abnormal protocols or traffic patterns in use on the network that will raise alerts within a security operations centre, as DNS and HTTP are two of the most common protocols in use within enterprise environments.
Fast-Flux
Another method that is used by malware authors to retain control of their acquired assets is to evade detection through a multi-tiered botnet architecture that rapidly switches domain, via a technique known as fast-flux domain switching. This is an innovative technique that has led to its continued usage in botnet command and control. The objective of this methodology is not so much to immediately confound detection capabilities, but more to evade the takedown capabilities of law enforcement organisations.
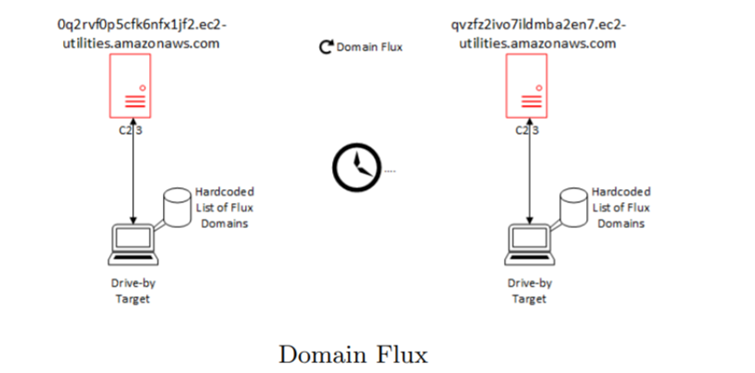

What is occurring in domain flux, is that the malware author will have pre-calculated a number of domains, using a domain generation algorithm. These domains will be issued to the target which is executing the malware. These domains are registered, either dynamically, or beforehand, and are switched between for the purposes of command and control. From a security analyst or system administrator’s perspective, this traffic will manifest itself as an abnormally large number of domains, to which a system is connecting.
Double-Flux
Double-Flux is another innovative malware network traffic obfuscation methodology. The way in which this works is by changing the DNS NS records as well as the DNS A records, which is termed double flux. The most famous example of Double-Flux being used as an anti-forensic methodology is the Avalanche network, where, according to Europol, 5 individuals were arrested, 37 premises were searched, and 39 servers were seized. Victims of this malware infection were identified in over 180 countries.
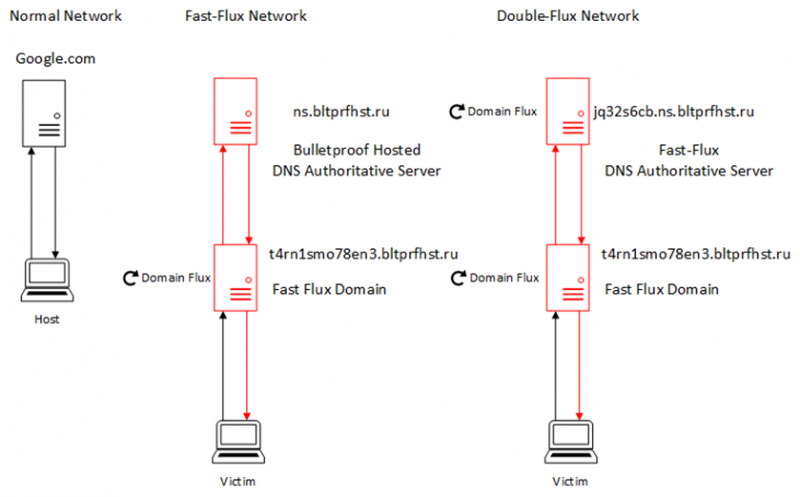

Double flux, in practical terms, is a more complex and resilient method of obscuring command and control communications than single-flux. This is where the root domain of the malware’s command and control server will have a DNS name server assigned to that domain, which is also rapidly switching in a fast-flux methodology.
Conclusion
As can be seen from this blog post, there is a constant arms race between malware authors and malware analysts, in terms of forensics and anti-forensics. This results in a variety of specialised tools and innovative methods being used by both sides in a reactive manner.
Like what you see? Share with a friend.




