Risk management is at the heart of information security and should be at the forefront of an organisation’s information security program. The term risk management covers all the activities associated with identifying, quantifying, and addressing the risks associated with threats and vulnerabilities.
In security a risk is defined as the potential for negative impact on an organisation, its goals or objectives, or its assets (people, data and systems) when a threat exploits a vulnerability.
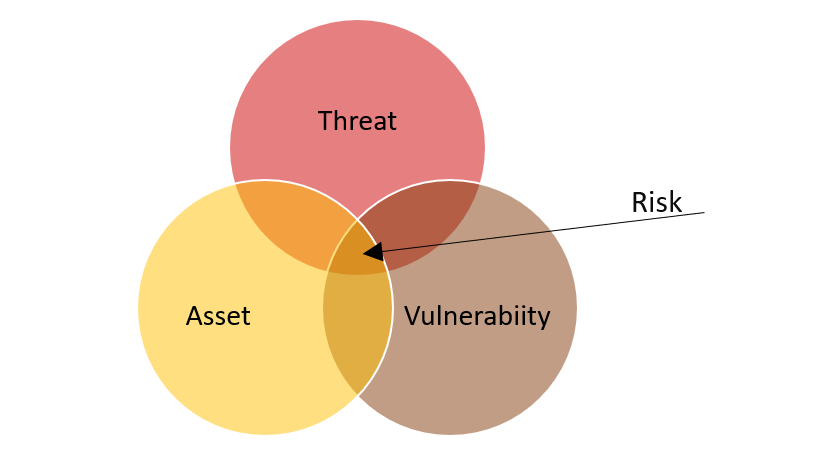

A risk assessment is the combination of activities involved in identifying threats and vulnerabilities and determining both the impact and the likelihood of those threats exploiting the vulnerabilities identified.
There are many risk frameworks that provide guidance on the conduct of risk assessments but in general a risk assessment will include the steps shown below.
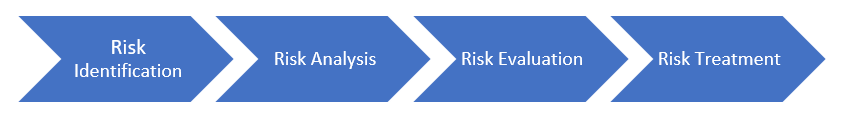

Risk Identification
The first step is to identify and determine the value of your assets. This includes identification and classification of your data based on its sensitivity or value to your organisation. During risk identification you find the assets that need protecting and the vulnerabilities and threats that pose a risk to those assets.
Risk Analysis
Risk analysis should always start with a vulnerability assessment and a threat analysis. This stage is focused upon assessing the likelihood of threats exploiting vulnerabilities in your environment and establishing the impact to your assets if that occurs.
Risk Evaluation
When completing a risk evaluation the results of your risk analysis are compared with your organisations defined risk tolerance (how much risk your organisation is willing to accept). You are then able to determine the best course of action to take for each identified risk.
Risk Treatment
When you have identified and assessed the threats, vulnerabilities and risks to your organisation you need to determine the best method to address each risk. This process is known as risk treatment. There are four main types of risk treatment: avoid, mitigate, transfer and accept. Each of these are decisions taken by management with guidance from the organisation’s security team.
Avoid
Risk avoidance involves removing the risk by stopping or removing the activity or technology that causes the risk. Risk avoidance is chosen when the level of risk exceeds the agreed acceptable risk tolerance but is difficult to achieve without causing disruption to the business.
An example of risk avoidance could be to ban the usage of personal cloud storage services to prevent data loss through unauthorized data copying.
Mitigate
Risk mitigation is the most common strategy and involves reducing the likelihood of a threat being realised or lessening the impact on the business of a realised threat. Risk mitigation involves the implementation of policies and technologies to reduce the damage that a risk might cause.
An example of risk mitigation could be to deploy multi-factor authentication for access to sensitive data or systems.
Transfer
Risk transference involves moving the responsibility and potential loss associated with the risk on to a third party. The most common form of risk transference is insurance.
An example of risk transference could be when a cyber breach causes a company to lose customer data. The company would rely upon the insurer to cover any financial loss caused by the breach. However, the company itself must manage any reputational damage.
Transference of all risk is difficult to achieve. Risk sharing is a modern approach where companies use cloud-based services as the risk is then shared between the customer and provider.
Accept
Risk acceptance is the process of accepting the risk that is associated with a particular threat. Risk acceptance is the correct strategy if avoiding, mitigating or transferring a risk would cost more than any expected losses from a realized threat. A risk should only be accepted if it is within the organisations risk tolerance or appetite.
Summary
Risk assessment and risk management are vital to effective information security management. There are many risk management frameworks to choose from, depending on the size, culture, and sector of the organisation. These frameworks, including ISO/IEC 27005, NIST Special Publication 800-37 and COBIT are all designed to provide internal controls that bring risk to an acceptable level.
