In a recent penetration test ResourceLink version 20.0.2.1 was found to be vulnerable to local file inclusion (LFI). ResourceLink is a payroll web application that allows HR departments to manage payments and employees’ bank account details.
LFI allows an attacker to include the contents of another file hosted on the web server, within a web page. Only files to which the web service has read access can be included.
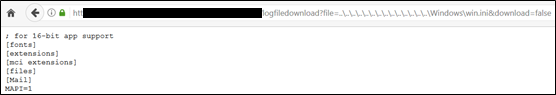
The vulnerability exists in the “logfiledownload” parameter which is part of the ResourceLink support section included within the ResourceLink application. The support section was accessible with default and weak credentials (support/support). The vulnerable parameter allows an authenticated user to view logs of the web application. However, an attacker can abuse this functionality to read files on the server, such as “C:\Windows\win.ini”, as shown below.
An attacker can exploit this vulnerability to read files containing sensitive information stored on the server, such as clear text credentials or session cookies. The following example shows it was possible to retrieve JSESSIONIDs, URL session IDs, and clear-text passwords from a log file:
https://[redacted]/support/logfiledownload?file=..\..\logs\server.log&download=false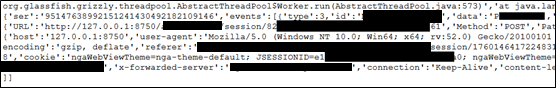

Furthermore, an attacker can abuse this vulnerability to read the SQL connection string, which contains the credentials that ResourceLink web application uses to connect to the Oracle database:
https://[redacted]/support/logfiledownload?file=..\..\config\domain.xml&download=false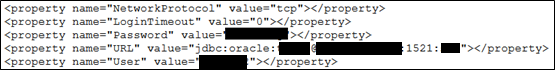

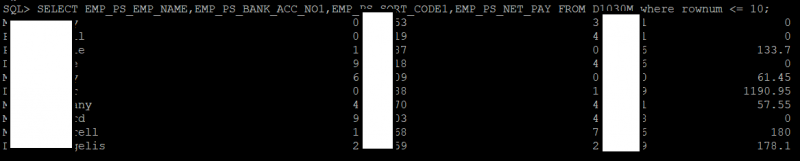
As result, this would allow an attacker to access data stored in the Oracle database such as bank account details:

Vulnerability Disclosure Timeline
08/08/2018: Initial contact to the vendor using the contact form on the vendor’s website.
08/08/2018: Software developer director contact details were found on vendor’ website and was contacted directly.
03/09/2018: No response was received and a last call email was sent to the vendor.
11/09/2018: The vendor replied asking for further details.
21/09/2018: Established a telephone call with the vendor who confirmed the vulnerability.
30/10/2018: The vendor confirmed that vulnerability is now fixed in release 20.
08/11/2018: CVE-2018-18863 vulnerability was disclosed.
Like what you see? Share with a friend.