Introduction
There’s that old saying, “sometimes you need to go backwards in order to move forward”.
Cyber criminals, known to operate at the bleeding edge of technological innovation to outwit their white-hat counterparts, have taken this advice and returned to techniques that were commonplace in the mid-to-late 1990s. Macro malware has been on the rise over the past couple of years, but unlike the 90s, the authors now include sophisticated APT threat actors working on behalf of organised crime syndicates and nation state entities; something which makes this throwback threat all the more serious the second time round.
Responding to the revival of “old skool” document-based malware, in March 2016, Microsoft announced a new feature in Office 2016 that can block macros and help prevent infection in enterprise environments. But before we look at this and other defensive strategies, let’s explore the phenomenon a bit deeper.
Macro Malware
The latest research by Radicati predicts that 116.4 billion business emails will be sent and received this year. A significant portion of these are likely to include some sort of file. Whilst end-users have grown suspicious of attachments which end in extensions such as .exe (many email filtering systems will also drop these automatically), far fewer will be cautious of opening Office files such as Word, PowerPoint or Excel documents. These files are after all routinely exchanged by organisations, both internally and externally, and are considered part of the modern business ecosystem. What few users realise however, is that these files can harbour malicious code in the form of macros.
Macros in Office documents are scripts written in Visual Basic for Applications (VBA) which are used for automating common tasks. Macros have genuine uses, saving users the expense of having to go through long, complex and repetitive routines, but the versatility of VBA also allows for activities such as reaching out to distant web servers to silently download and run malicious executables. It used to be that Office programs allowed macros to run automatically, whenever a document was opened. In more recent versions, however, macros are disabled by default; something which effectively saw this threat drop off the radar at the turn of the millennium.
Social Engineering
Social engineering (SE) is a term that crops up a lot in the security discourse, and for good reason. Attackers are leveraging weaknesses in the human element of security to obtain maximum gains. And it’s SE that’s making this particular threat so prevalent and in vogue again. To convince users to enable the macros, the aspiring intruders typically craft their emails so that they appear to be from a trusted business partner or colleague. They attach their file and kindly request the user to click the “Enable Content” option under the pretence that this is required to view the contents properly.
Examples of Phishing Campaigns
The following screenshots were taken from a recent phishing campaign Dionach undertook for a client who wished to assess their susceptibility to remote compromise. These examples incorporate the strategies widely harnessed by the real cyber criminals. The email content is professional in character and tone, whilst the action being requested is perfectly plausible. Note the final line, which explicitly instructs the user to enable the macro.
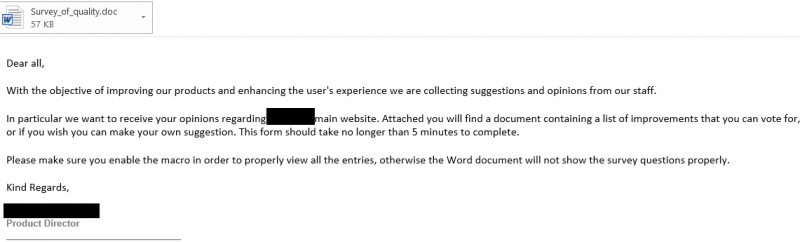

Once a user opens the document, they will be presented with the following:
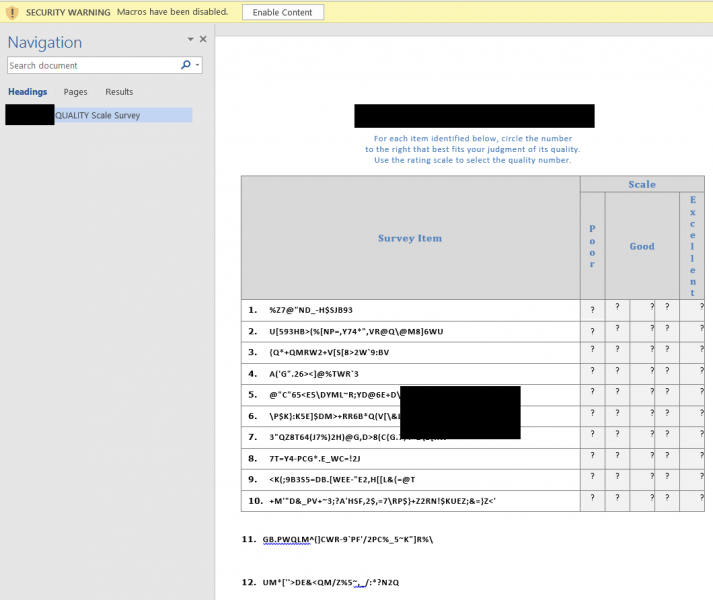

As predicted in the email, the content appears to be malformed, and we receive a warning that the macros have been disabled. In this example, if we were to proceed by clicking the “Enable Content” option, as instructed by Fred, our trusted Product Director, (spear-phishers frequently conduct research on their target companies) the VBA macro would invoke a PowerShell script which in turn would spawn a command shell on the victim user’s machine.
At this point, the attacker has complete control over the user’s computer. If this machine is domain-joined, there are a multitude of techniques an attacker could employ to quickly escalate their privileges and gain command over the entire corporate network.
When testing, Dionach has had a great deal of success utilising macro malware in campaigns similar to the one above, but unfortunately so too have malicious actors. Exploiting trust is a key enabler for cyber criminals, and with this threat it’s the general misplaced belief that these file types are inherently benign that’s paying off handsomely for the cyber underground. The rate at which these harmful files are being released into the wild is steadily increasing, with malicious macros featuring in many recent high profile incidents, including last December’s hack on the Ukrainian power grid, which temporarily left more than 230,000 residents in the dark, as well as in the notorious Dridex banking trojan campaign.
What Can We Do To Prevent This?
So, what can be done to help thwart this threat at the end-user and enterprise levels? The following are certainly good ways to start:
Staff Training
All staff should undertake regular information security and phishing awareness training. We need to move away from the idea that all phishing emails are misspelt messages purporting to be from West African princes, promising great fortune in return for a small favour. Today’s most persistent and dangerous threat actors are highly organised and they do their homework. They scour through social media to find out who you’re connected with, research your suppliers and clients and use email spoofing tricks to make you believe the contact is a trusted source. An email which claims you have to “enable content” to properly view the document is almost certainly unsafe, and reminders like these can help to keep hackers on the outside of your network.
Training users how to spot suspicious emails and the reporting procedure when received and/or get actioned should be a priority for every business.
Ensure Macros Are Disabled by Default
Verify that macros are disabled in your Microsoft Office applications. Whilst this has long been the default setting there is no harm in double checking. In enterprise environments, system administrators can issue the default setting for domain users. The following article may prove useful here:
Remember this step alone will not prevent users from choosing to enable the macros themselves.
Block Files with Macros
Some network protection and anti-malware solutions offer to block Office documents arriving from the Internet via email if they contain macros. Consider enabling this option. Remember that macros are essentially small programs embedded into documents and there are few instances where outside parties should need to send you such items.
Make use of Office 2016’s New Feature
As mentioned earlier, Microsoft has introduced a new tactical feature in the latest version of Office that blocks macros from loading in certain high-risk scenarios. As is explained in the link below, this feature has been designed to do the following and can be controlled via Group Policy:
- Allow organisations to scope macro use to a set of trusted workflows.
- Actively block macros in scenarios considered high risk.
- Provide end users with different and stricter notifications to help them distinguish between a high-risk situation and a normal workflow.
Reporting is Thwarting
All too often, staff fail to report suspicious emails. If you or your team receives such an email, ensure a relevant member of staff is notified. By staying silent, other targeted users within the organisation may fall for the ruse and introduce malware into the network. Policies should be in place to support this practice.
Perform Regular Anti-Malware Scans
Anti-malware solutions, although not a panacea, are often effective in detecting, preventing and cleaning-up harmful programs. Although heuristics are playing an increasing role in these products, these technologies still widely function according to a blacklist, signature-based model. New and advanced malware can therefore circumvent these products to remain in your environment undetected. This should not, however, deter you from running regular scans and keeping your definitions up-to-date.
Undertake Penetration Tests
A good way to assess your security posture and implementation of the above practices is to sanction a social engineering penetration test from a recognised provider. The results from these tests are great indicators of where your current strengths and weaknesses lie, enabling you to address any issues that may be uncovered.
Summary
Microsoft’s decision to change the default macro setting dramatically curbed this threat at the turn of the millennium, and the vendors continue to devise new solutions. End users and organisations, however, should also do what they can. Following the above recommendations won’t make you immune from the threat of macro malware, but it can certainly reduce the impact and likelihood of compromise.
Like what you see? Share with a friend.



