Social engineering attacks are becoming increasingly popular amongst attackers, as a strategy to breach companies. Verizon carried out a study on social engineering attacks and found that over 43% of breaches that were documented involved some form of social engineering attack.
There is a reason why social engineering attacks are becoming an increasingly common attack strategy amongst cyber criminals, as these types of attacks have the most success when it comes to breaching organisations. The most common themes in phishing attacks come from those which relate to current political or social events, natural disasters, or those which attempt to impersonate staff members, such as an IT support technician. According to a report by APWG, titled “APWG 2016 Q4 Phishing Trends”, the number of phishing attempts against organisations increased by 250% between October 2015 and March 2016. It is evident that this form of social engineering is the most exploited by attackers to gain access to organisations.
Social engineering attacks can come in a variety of different forms, in relation to email phishing; two types of attacks exist, untargeted and targeted.
Target phishing attacks involve an attacker using personal information, which it is specific to an individual or a small set of individuals. An attacker may use information relating to personal aspects of the victims life such as an event or incident which has occurred, coupled with tricks to ensure that the phishing email appears to be legitimate. These techniques could include impersonating a trusted source or person such as an IT support employee, or someone of a higher authority. Additionally, attackers will also attempt to influence their victims by exploiting emotional characteristics such as fear.
Untargeted phishing attacks tend to be less specific and are aimed more towards a variety of people, and involve generic emails such as those which include links to videos, articles, or websites, which ask for financial payments.
Dionach conduct a number of social engineering services, which are becoming increasingly more popular with clients due to the trend in security breaches involving social engineering attacks. The following graph illustrates statistics showing the success rates of both targeted and untargeted phishing campaigns, which Dionach have carried out:
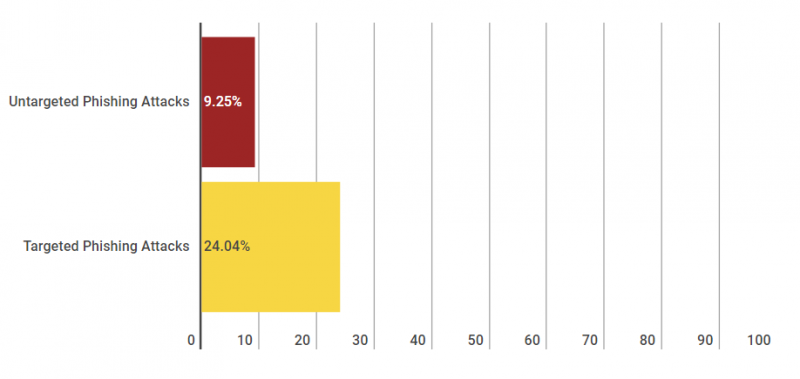

The graph above shows the success rates of each type of attack, when Dionach conducted untargeted phishing campaigns, only 9.25% percent of victims clicked on a malicious link. In contrast, when targeted campaigns were conducted, the success rate increased by half with 24.04% of victims clicking on malicious links. These numbers are not surprising, as targeted campaigns in theory should present more success, however organisations are still falling victim to simple and blatant phishing emails.
How do we protect ourselves against these types of attacks? In today’s blog post, we will look at an example phishing email, which illustrates the types of techniques that attackers use when they are trying to socially engineer their victims into performing actions on their behalf. We will then analyse the email and discuss the various areas one could inspect to determine the legitimacy of an email.
To provide some context, we have an attacker called Tom Fisher who has performed some reconnaissance on an employee called Emma Jefferson. From Fisher’s research, he has determined that Emma is a keen runner and recently participated in the Bournemouth marathon. Using this information, Fisher has tailored the following phishing email in an attempt to entice Emma into providing her personal details to Fisher, as well as access to her computer through an Office macro:
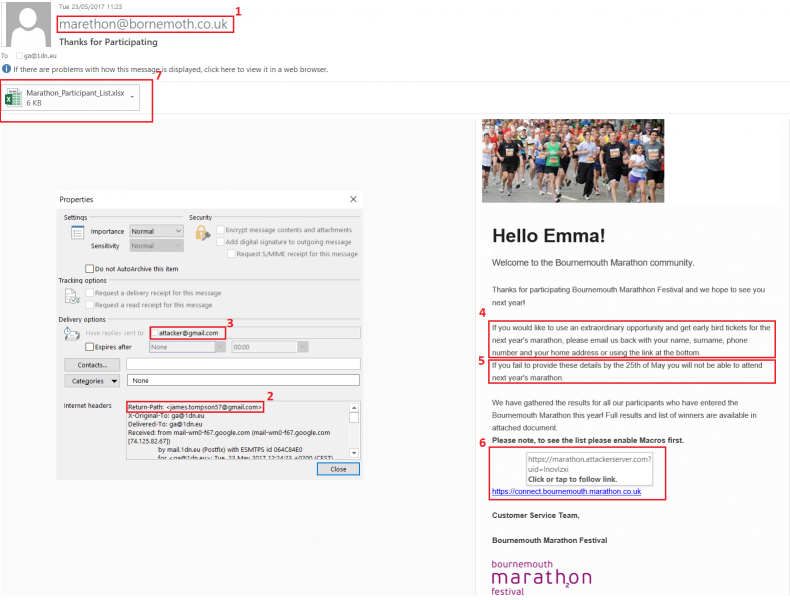

As we can see from the email above, there are a number of elements which one can inspect to determine whether the email is legitimate or not. The following bullet points summarise the structure and content of a phishing email:
- Misspellings in email addresses
- Check if the sender in the email header matches that which is in the actual email
- Reply to email address is a different from that of the claimed organisation’s one
- If the email requests personal information, like a credit card number or user credentials for accounts such as Amazon
- If the email contains some warnings in order to put a victim under pressure
- If the email contains some links which after hovering over them reveal different URLs
- If the email contains a malicious attachment such as an Office document which includes a Macro, or asks the user to download and run a program from website URL
A number of phishing emails will contain offers to deals in an attempt to entice victims into clicking on malicious links. To avoid this, check that the offer exists with the legitimate company.
As we can see, identifying these types of attacks can be difficult if people are not educated and aware of them. Attackers will continuously innovate their phishing attacks and create new ways to trick users into performing actions on their behalf. I hope that this article has helped to provide some insight and education into phishing emails to help better protect organisations against these types of attacks.
Like what you see? Share with a friend.




