Encryption in mobile devices is tricky and often developers do not fully understand the mechanisms that iOS and Android, the most common operating systems for mobile devices, provide to ensure data stored on the devices remains relatively secure.
In this blog post I will briefly discuss the current status for both operating systems and highlight the main differences, which mainly boil down to the fact that on iOS files get encrypted on a file-by-file basis (FBE – File Based Encryption), as opposed to the traditional approach that Android has taken to encrypt the entire disk (FDE – Full Disk Encryption).
iOS
The following diagram, taken from the latest version of Apple’s iOS Security Guide, gives a good idea of how encryption works.
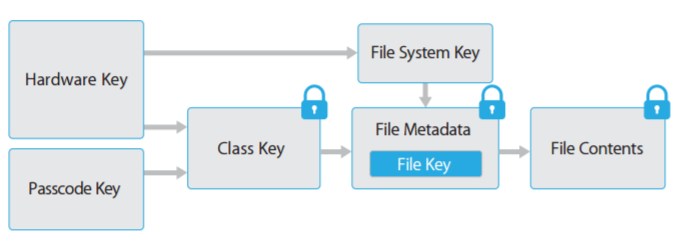

Figure 1 https://www.apple.com/business/docs/iOS_Security_Guide.pdf
Every file goes through a few iterations of encryption, which combine hardware and software based keys to ensure that brute-force attacks are difficult to carry out and are only possible on the device and not offline.
One of the most important things to note here is that as part of the encryption process every file has an associated data protection class, which allows developers to define under what circumstances the data is accessible. The available classes are as follows:
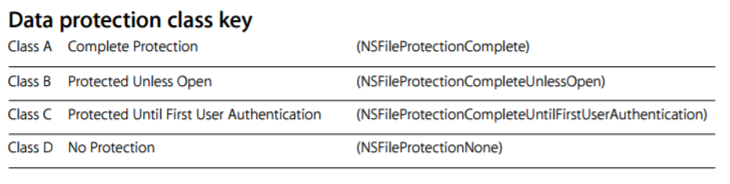

Figure 2 https://www.apple.com/business/docs/iOS_Security_Guide.pdf
The above classes allow developers to use fine-grained permissions when encrypting data, and is considered a well-designed and robust approach.
Android
Traditionally, Android followed a more rudimentary approach to encryption, and up to version 7.0 only gave the option of encrypting the entire disk (FDE – https://source.android.com/security/encryption/full-disk). The below diagram summarizes how this works:
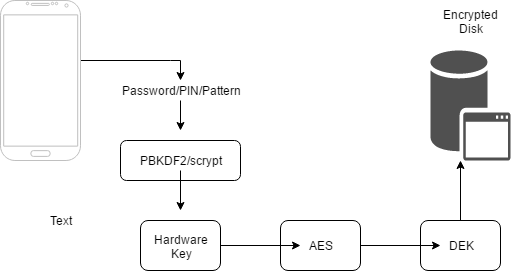

Figure 3
Even though after version 5.0 the design was improved to add hardware support (TEE – Trusted Execution Environment) and prevent offline brute-force attacks, full disk encryption does not provide the granularity that iOS offers. In order to address this issue, Android’s latest version (Nougat – 7.0) does now support file based encryption (https://source.android.com/security/encryption/file-based). This implementation is still at an early phase, and there are many things that are still to be implemented, however something similar to what iOS offers can be implemented by combining existing features such as the Keystore System (https://developer.android.com/training/articles/keystore.html).
To summarize, it is evident that Apple took time when designing encryption for iOS, and as result, its current implementation is considered to be a more robust and better approach. Android arguably made some initial mistakes in its design, and adding to that the variety of vendors and modified versions of the base OS (Android Open Source Project – AOSP) that have been released since then, makes harder to get back on track. However, decisions taken in recent versions of Android show that Google seems to be going on the right direction, although it will take some time to get there and catch up with iOS in terms of storage encryption security.
Like what you see? Share with a friend.




