When deciding whether or not to install iOS 12, many iPhone and iPad users will be primarily concerned with the “flashier” features: Memojis, group FaceTime calls, performance improvements for older devices, and more. However, the recent iOS update also contains a number of security features that deserve some consideration for those concerned about protecting the data stored on their iPhones. In this blog post, we will consider several of the iOS 12 security features and their relationship to mobile application developers and end users.
Security Code AutoFill
We are frequently reminded to make use of two-factor authentication to increase our security in case of a password compromise. Many applications, from social media to mobile banking, will permit or even require users to enter both their password and a one-time security code, sent via SMS or an authenticator app, in order to log in. The iOS 12 security code AutoFill feature is Apple’s attempt to encourage more iPhone users to adopt two-factor authentication in their apps. When certain keywords indicate the presence of a message containing a one-time security code, the iPhone will offer a one-tap keyboard option to automatically populate the relevant field with the code’s value. This is shown below, in the Telegram Messenger application:
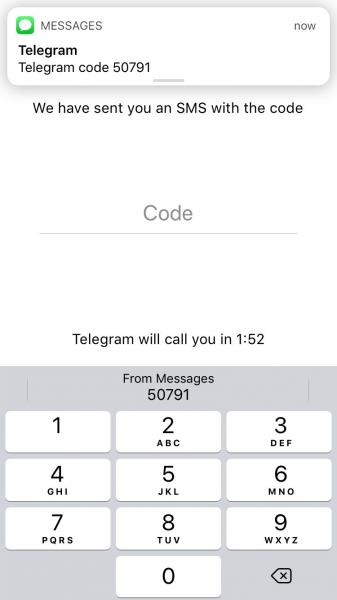

While encouraging the use of two-factor authentication is an excellent way to increase the difficulty of account compromise, SMS is widely considered a weak form of two-factor authentication and has been criticised by researchers and organisations such as the U.S. National Institute of Standards and Technology (NIST). In the past, attackers and researchers have intercepted SMS messages in transit and social engineers have convinced phone service providers to redirect SMS messages to their own devices. Both attacks have allowed the theft of secrets such as security codes.
That said, the National Cyber Security Centre (NCSC) has stated that even weaker modes of two-factor authentication options are preferable to a lack of two-factor authentication, so the security code AutoFill feature could provide a net benefit for many users initially reluctant to adopt two-factor authentication. Developers should thus consider this feature as an opportunity to integrate two-factor authentication into their own mobile applications while also encouraging users to choose more secure options such as authentication applications rather than defaulting to SMS. Users, for their part, should carefully consider all the two-factor authentication options offered by their favourite applications and choose the option that best fits their own security.
iCloud KeyChain
In an effort to improve password management solutions, iCloud Keychain functionalities will expand in iOS 12. iCloud Keychain will now offer to generate random passwords in Safari and iOS mobile applications and store these passwords automatically in the iCloud Keychain to be viewed, edited, or AutoFilled into relevant form fields later. iCloud Keychain will also flag any passwords that appear multiple times with a small grey warning triangle, as shown below:
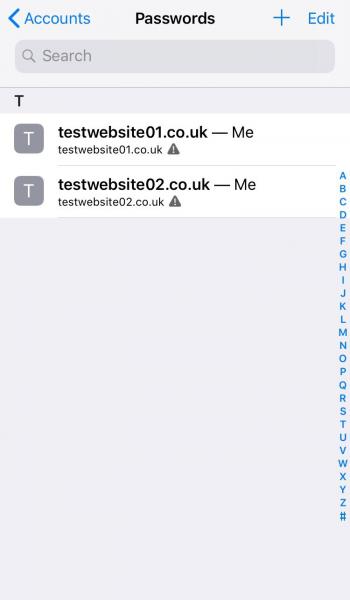

Additionally, iOS 12 will now allow users to AirDrop passwords stored on iCloud Keychain and third-party password managers to nearby Apple devices. AirDrop uses the Bluetooth Low Energy (BLE) protocol to initiate a pairing between sender and receiver. The paired devices then create a TLS 1.2 encrypted connection to transfer data.
Using password managers has become an increasingly popular way to help users generate long and complex passwords to protect against brute-force attacks. Additionally, as password reuse can exacerbate the effects of a phishing attack or data breach, reminding users when they use the same password on many different websites and applications can help to increase security.
It should be noted that Yanick Fratantonio and a team of researchers recently discovered that many mobile password managers for Android offer an autofill option for malicious mobile applications impersonating legitimate ones, which could facilitate attackers performing social engineering attacks. Fratantonio has since stated that iOS 12 appears to require developers to use a mapping function (“apple-app-site-association“) that associates mobile applications with websites in order to prevent this issue. However, additional research and auditing of this functionality (and any ways to bypass it) is likely necessary.
Users should consider many available options before selecting a password manager. iCloud Keychain does not function cross-platform, so it may not be the ideal password management solution for a user who owns many non-Apple devices. Additionally, some third-party password managers come with additional auditing features that evaluate the strength of chosen passwords. Users must also decide whether they prefer their password manager to store all information locally or back up the data to an external service such as iCloud, which adds extra convenience in case of a lost device but increases the attack surface.
Mobile application developers should support the use of password managers but should not assume that users will always use a long, complex, and randomly generated password when registering an account. Implementing restrictions such as password complexity requirements and account lockouts can help to protect against brute-force attacks, which could compromise accounts using weak passwords.
Providing users with a quick and easy way to send passwords over an encrypted channel, for example AirDrop, is also likely a step forward for secure password management. However, more formalised systems of password sharing (such as those offered by many password managers) are likely preferable for collaborative environments in which passwords are frequently shared and many users do not own Apple devices.
FaceTime Encryption
According to Apple, both one-on-one and new group FaceTime calls will be encrypted end-to-end in iOS 12. Connected devices will begin by establishing a shared secret, which they will use to derive the session keys. The keys will in turn be used for the Secure Real-Time Transport Protocol (SRTP) connection, each packet of which is encrypted with AES-256 in Counter Mode and HMAC-SHA1.
There is nothing obviously insecure in the above protocol, which is described further in Apple’s security guide. It should be noted, however, that implementation is key in cryptography – and sometimes, the implementers get it wrong. As a result, additional research and testing by cryptographers is necessary to ultimately determine the security of this protocol. That said, expanding avenues for secure communication is a noble goal, and users may want to factor in support for encryption when choosing video chat clients such as FaceTime or third-party applications.
Conclusion
While iOS 12 includes a number of security features not discussed above, the ones we have explored are likely to impact mobile application developers and end users the most. Both of these parties should consider these features, as well as their third-party equivalents, when creating and using mobile applications that store sensitive data. Although extended research and testing are still necessary to determine whether these features will properly protect end users from a number of security concerns, iOS 12 has likely been a step forward for the security of authentication and communication on Apple devices.
Like what you see? Share with a friend.




