What is social engineering?
Social engineering is the process of manipulating people into revealing sensitive information, obtaining access to restricted areas, or performing actions that may be beneficial to an attacker. Social engineering can be carried out using various tools and techniques, but is acted upon mainly via phishing emails, phone calls and physical intrusion.
Why is it a problem?
Social engineering poses a great threat and challenge to most organisations because their employees are sometimes the only barrier between an attacker and the organisations data or intellectual property, and exploiting people requires minimal resources and potentially a low level of technical knowledge.
Social engineering is a common way to gain an initial foothold within a target organisation’s network. With just a carefully crafted email, an attacker can compromise an employee’s workstation, which could then be used for further attacks within the internal network.
What is the significance of social engineering attacks?
Ponemon Institute and Accenture recently produced a comprehensive “Cost of Cybercrime Study” study[1], which covered 355 organisations in 11 countries and 16 industries. The study examined the impact and the cost of various cyber attacks against the observed organisations over a period of two years. The results show that social engineering attacks increased by 16% within one year and cost the companies a total of $1.4 million US dollars in 2018. The cost includes business disruption, information loss and revenue loss. Additionally, social engineering attacks may lead to a compromise of confidential data and intellectual property which could cause great loses to a business.
Walkthrough of an example attack
Objective
During one of our social engineering engagements, we performed a successful attack against a medium size financial company. The goal of the social engineering engagement was to test the susceptibility of the company’s staff to email and phone phishing.
Reconnaissance
The test began with reconnaissance tasks including subdomain enumeration, which revealed several publicly exposed services such as VPN and email portals. Inspection of the portals showed that the VPN login page required two-factor authentication (2FA) token to authenticate, whereas the email portal did not appear to require 2FA.
Further reconnaissance showed that the company’s domain was missing the SPF (sender framework policy) record, which is a simple security control to help detect spoofed emails[2]. This provided the opportunity to impersonate the client’s staff when creating phishing emails, which greatly increases our chances of successfully socially engineering a victim.
With a help of various open-source intelligence tools, it is possible to collate a comprehensive list of work email addresses belonging to the client’s staff. Information obtained from social media networks can also tell us a lot about the technologies used within an organisation, a company’s organisational structure, and specific individuals we may want to target in our phishing campaign.
The reconnaissance phase of the test therefore helped us to identify weaknesses in the client’s infrastructure configuration, the technologies in use as well as a potential target list – crucial information for a successful social engineering campaign.
Execution
The next steps involve preparation of the phishing campaign infrastructure and the creation of the phishing emails. As mentioned above, we chose to target the email portal; therefore for this test we created a fictitious email portal shown below. This was a clone of the client’s email portal.


The following screenshot shows the email that was sent out to our list of targets. Note that based on information gathered during the reconnaissance phase, we chose to impersonate “Bob”, who is a systems administrator. Furthermore, to make the email look more credible, we use a pretext in which we ask people to help identify issues with the organisation’s email systems. Finally, the hyperlink to the fictitious email portal is obfuscated to look like a legitimate company’s email link.
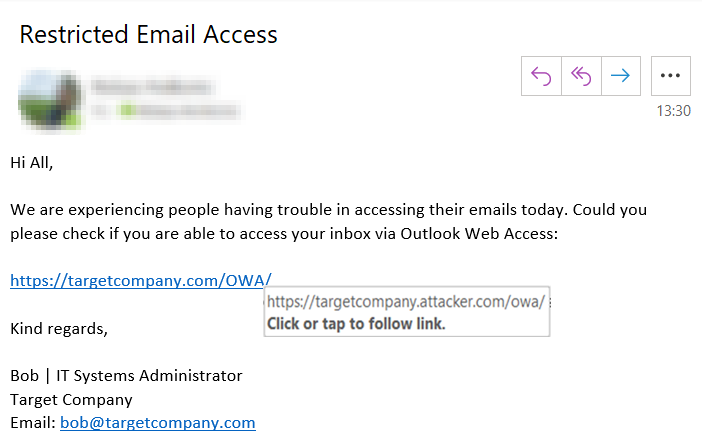

After crafting the phishing email and hosting the fictitious email portal on our server, we launched the phishing campaign against the client’s staff. Within the first view minutes, a number of clicks on the malicious link were registered. Shortly after that, a number of usernames and passwords were harvested via the fictitious login portal. In order to test whether the harvested credentials are correct, we attempted to authenticate against the genuine email portal. Unexpectedly, after a successful authentication using username and password, we were greeted by a 2FA authentication login page. The page allowed users to choose a 2FA method, with options including a phone call, a text message and a notification pop-up on their corporate mobile phone where a user can either approve or reject the 2FA request.
Since we could not get a complete access to the email service, this was a great opportunity to test the users’ susceptibility over the phone. A few of the client’s staff members were targeted using the following script in order to convince the victim to approve the authentication request to the email service.
Hi [Employee Name], This is Dave calling from [2FA Vendor]. I am assisting Bob today to troubleshoot email issues you are having. As you may know, some users are unable to authenticate using [2FA Vendor] two-factor authentication. Would you be able to help me out today? [Positive Response Received] You should shortly receive a pop-up notification on your [2FA Vendor] mobile application asking whether the authentication request should be approved. I will need you to test whether the application works correctly by approving the first authentication request.
In the script above we have continued using a pretext where we ask people for help. Christopher Hadnagy[3] discussed that willingness to help can be easily exploited because people like to help others. Using the pretext where we impersonate 2FA vendor staff, we managed to convince several people to approve our 2FA requests, which provided us access to corporate emails! This provided us with plethora of sensitive and business critical information that may be used in further attacks or monetization.
In conclusion, this example shows that a fairly simple and low-cost attack can provide an initial foothold within the corporate network and give access to confidential information. Even though the target company had hardened external network infrastructure and multi-factor authentication mechanisms, it was still possible to easily gain unauthenticated access to sensitive company resources. While the scope of the test allowed us only to access the aforementioned services without further compromising internal resources, in a real-world scenario this would be only the beginning of a potentially devastating attack. As an example, an attacker with email access could setup malicious outlook rules to monitor internal communications and perform phishing attacks from within a company to compromise workstations, thus gaining further access to the corporate network.
Mitigating the risks
The previous example shows us that with very little preparation and time we can gain access to sensitive company’s resources. However, we should now take a look at common information security pitfalls and learn how we can mitigate the risks and the impact of these types of attacks. The following issues should be addressed with a defence in depth mindset and implemented together rather than individually. Addressing the following issues should help an organisation to improve their security posture and reduce the likelihood of successful attacks from low-skilled attackers.
Email spoofing countermeasures
To prevent email spoofing, organisations should consider implementing anti-spoofing controls such as Sender Policy Framework (SPF)[4], DomainKeys Identified Mail (DKIM)[5] and Domain-based Message Authentication, Reporting and Conformance (DMARC)[6]. These countermeasures will prevent spoofed emails from reaching targeted individuals, thus reducing the chances of a successful phishing attack.
Implement an email filter
Additionally, organisations should consider deploying email filters. Core features of an email filter include automatic scanning of incoming emails for malicious attachments, content, and URLs. Emails that are deemed malicious are then quarantined so they do not reach recipient inboxes. Email filters reduce the amount of spam and malicious emails reaching corporate email inboxes.
Train employees
It is important to inform users about the potential risks and the impact of social engineering attacks against an organisation. Protection of an organisation’s assets is the responsibility of management, the IT department, and the end-users within an organisation. Therefore, it is important to deliver regular social engineering training to end-users, facilitate reporting of suspicious emails and phone calls and perform periodic tests to determine users’ susceptibility to social engineering attacks.
Patch and harden hosts
It is common to find missing critical security patches on internal systems. Unpatched security bugs such as privilege escalation and remote code execution vulnerabilities allow an attacker with an initial foothold to elevate their privileges or move laterally within the corporate network. Patching internal systems on a regular basis and verifying that the patches have been installed successfully should be standard practice. Although these systems are not exposed externally and therefore will not be targeted within the first phases of a regular attack, they are likely to be exploited later to facilitate further attacks.
Segregate resources
To enhance the security posture, organisations should also review their network architecture and ensure that there is sufficient separation between different areas of a corporate network. Network resources should be accessible only by hosts that require access for their job role or function. Sufficient network segregation will reduce the attack surface by limiting the number of hosts that an attacker can reach from an already compromised host. Although there are plenty of techniques such as VLAN hopping for bypassing such network restrictions, network segregation will act as deterrent and will cost an attacker more time and resources when targeting the rest of the network.
Logging, analysis, and alerting
Organisations should ensure that there is sufficient logging at the network, host and service levels. Additionally, organisations should actively analyse logs for suspicious activity and have means of alerting relevant staff. Monitoring and inspection of logs may indicate malicious activity within a network, and an early indication of an incident will help to handle the impact of a potential attack.
Have an incident response plan, and test it
Attacks against organisations are inevitable, so every organisation should have a plan on how to respond to various incidents. It is crucial to have a clear and well-defined incident response plan that can be relied upon during a critical situation. The CERT Societe Generale[7] has produced a number of cheat sheets of best practises that could be followed when responding to an incident. Note that organisations should regularly test it to ensure that a plan is efficient and covers a number of plausible attack scenarios.
Conclusion
In summary, social engineering attacks are inevitable and they can have a devastating impact on businesses. However, organisations should focus efforts on mitigating the risk and the impact of a social engineering attack. This can be achieved by implementing a combination of appropriate security measures. Note that business cannot rely solely on either technical defences or end users to recognise and protect against security threats. Rather, the implementation of technical countermeasures and the involvement of staff members go hand in hand when defending an organisation.
[3] Hacking Hadnagy, C. (2011). Social engineering. Hoboken, N.J.: Wiley.
[5] https://www.gov.uk/government/publications/email-security-standards/domainkeys-identified-mail-dkim
Like what you see? Share with a friend.




