Flash is well-known to people within the cyber security industry to have a long history of security of vulnerabilities as well as functionality flaws. Since 2016, most web browsers have disabled Flash to automatically run on sites. In 2017, Adobe has finally gave up on what used to be one of its most popular products, and announced that support for Flash will officially end on 31st December 2020 (Adobe Corporate Communications, 2017).
However, it is impossible to completely uninstall Flash, as the plugin has been integrated in both Internet Explorer and Microsoft Edge, which are core applications that come with Windows builds. Therefore, the purpose of this blog post is to provide possible solutions for organisations to minimize the risks of having Flash.
Minimizing the Risk
For some developers it is possible to convert the content that would have been developed on the Flash platform to HTML5. HTML5 is an open standard web programming language that has been incorporated into all major web browsers and can deliver audio and video content without the security flaws or vulnerabilities that Flash has.
However, for others it might not be that easy as some content on the website can only be rendered on the Flash platform. There are a few methods that system administrators can choose according to organisational needs and suitability. For the purpose of this blog, a Windows Server 2012 R2 virtual machine and a Windows 10 Enterprise virtual machine are used to demonstrate methods that can be used to minimize the risks of using Flash.
This part of the blog will demonstrate how to implement those methods on both Google Chrome and Firefox, by using either one of the browsers as the sole browser for Flash player and disabling Flash on built-in browsers including Internet Explorer and Microsoft Edge. Google Chrome fortunately has its own administrative template, and Firefox can be distributed to workstations using a JSON policy template which makes it easier to manage websites and plugins on multiple workstations that have the browsers installed.
Chrome
Importing Google Chrome’s Administrative Templates
An administrator would need to have the Google Chrome Administrative Template installed in order to create the group policy which can be downloaded from the following link:
https://dl.google.com/dl/edgedl/chrome/policy/policy_templates.zip
Make sure to extract the zip file for the template and move it to C:\Windows\PolicyDefinitions, which is the default directory on the DC where the Group Policy Editor looks for Policy Templates.
The policies would automatically appear under Administrative Templates under Computer Configuration and User Configuration as shown in the image below:
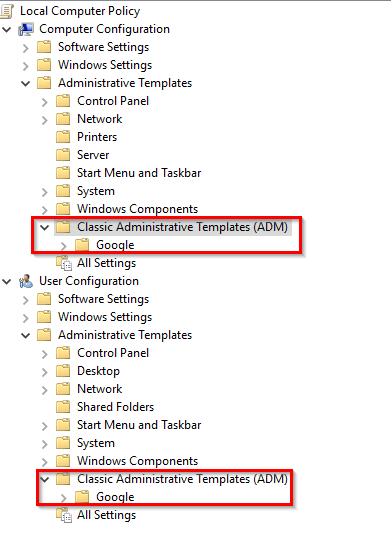

If the Group Policy Templates are saved in a different location, navigate to User Configuration > Administrative Templates and right click and select Add/Remove Templates:
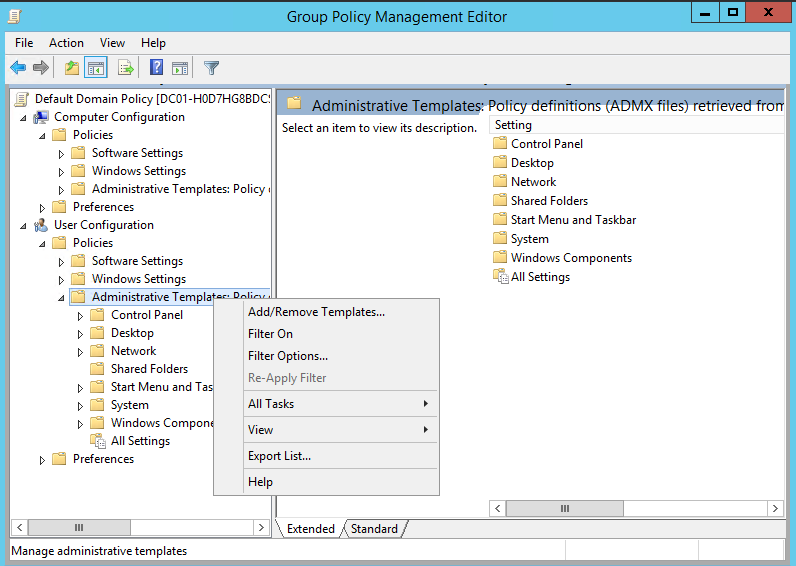

Click “Add” and import the en-GB language version of the chrome.adm file:
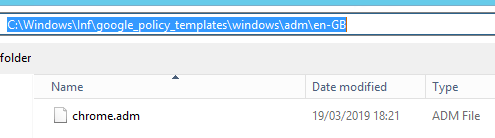

The Group Policy template will appear in the Add/Remove Templates window, click close to save the settings and “Classic Administrative Templates (ADM)” will appear at the bottom of the administrative template with Google Policy templates installed:
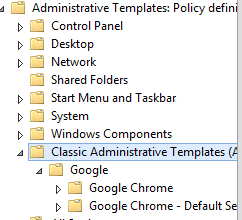

The same steps should be followed for the GoogleUpdate policy template, which is a policy template used for configuring updates for Chrome and plugins. The template can be found in the following link:
https://dl.google.com/update2/enterprise/GoogleUpdate.adm
Configuring the policies
Under “Google”, navigate to “Content Settings” under “Google Chrome”:

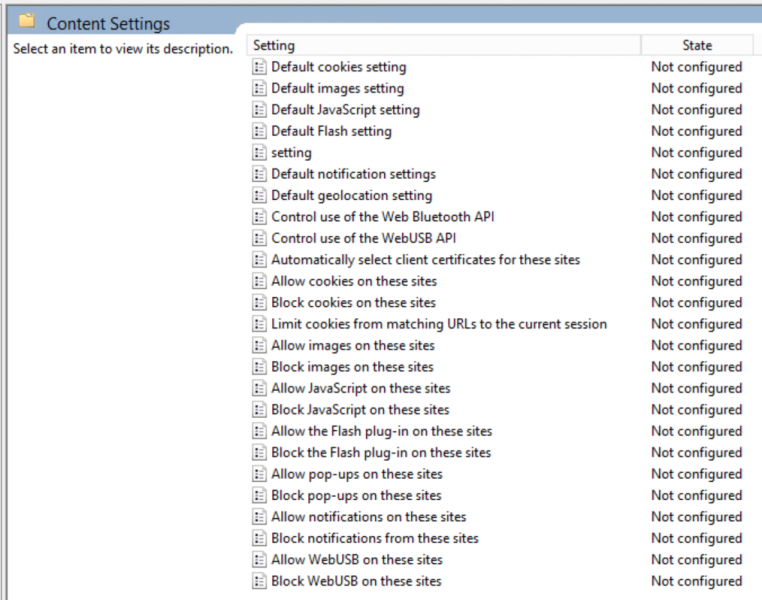

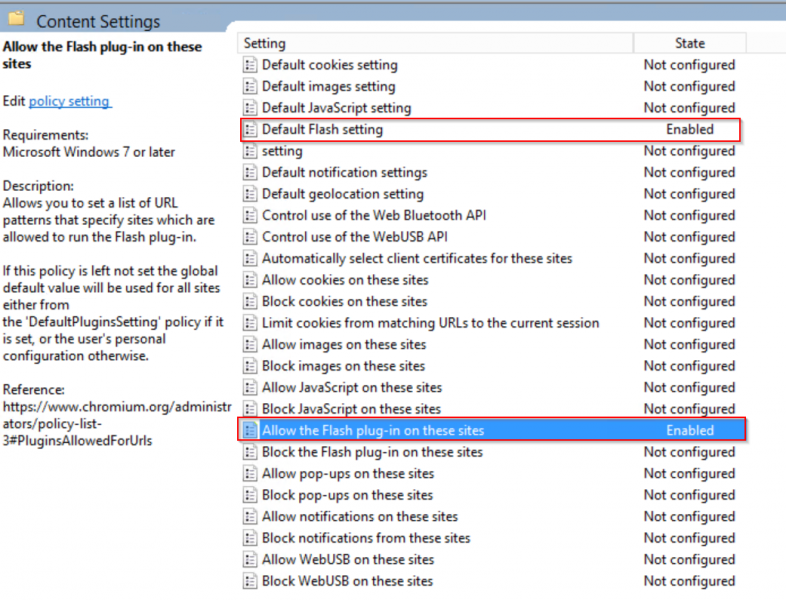
The image above shows the policies that system administrators can use to restrict the content shown for each accessible website whether on the internet or hosted internally. The next step will focus on configuring the policy “Default Flash setting” and “Allow the Flash plug-in on these sites” (GPO Edit, 2017).
Default Flash setting
Double click on the policy “Default Flash setting”, this setting falls under “DefaultPluginsSetting” in the Chrome administration policies. By default, i.e. in its “not configured” state, the global setting for the browser allows any user to manually change the settings which can allow any site to automatically run the Flash plugin, block the Flash plugin entirely or set the Flash plugin as “Click to play” which only allows the content to be ran manually when the user clicks on it. It is recommended that system administrators enable this setting, as shown in the screenshots below, to prevent users from modifying this setting on the browser, and to prevent websites that are not included in the whitelist to run Flash (The Chromium Projects, 2019).
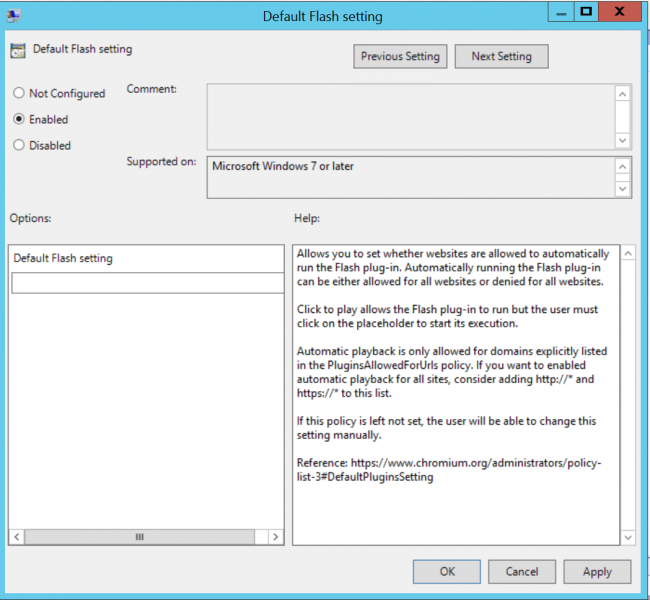

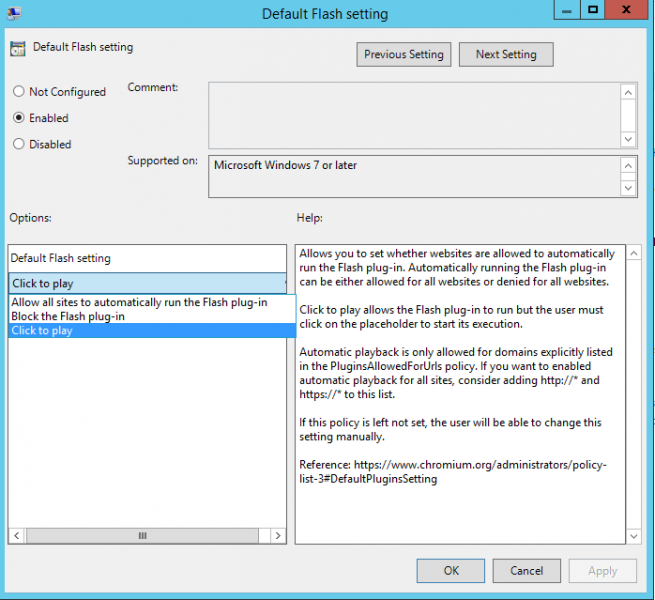
Once this is ticked, click the box below “Default Flash setting” and change it to “Click to play” so that Flash is allowed to run, however a user must click on the container to start the execution. Click “OK” to save and close this policy.

Allow the Flash plug-in on these sites
This is where system administrators configure the whitelist for Flash. Without this setting configured, the browser will use the global default value either from “DefaultPluginsSetting” which was discussed previously, or user’s personal configuration that can be set from the browser. This setting needs to be enabled in order to create a whitelist. An administrator will then select “Show” to show the current whitelist and edit when required by adding URLs under the “Value” column, as shown below.
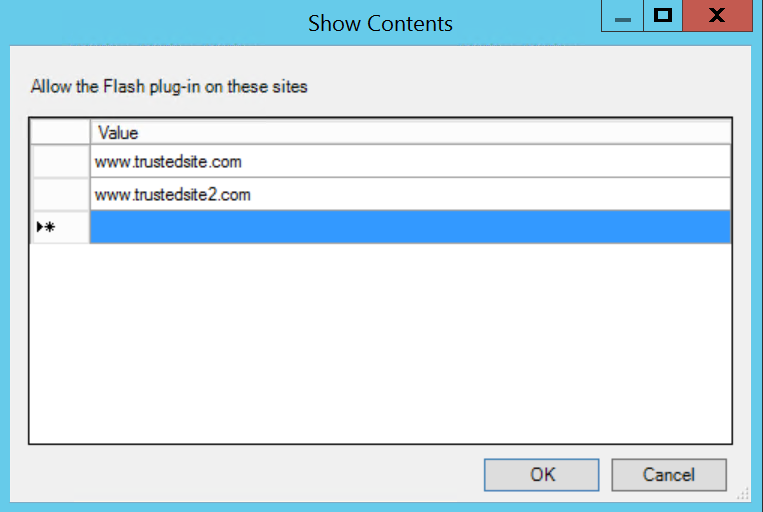

Once this is saved, the “Content Settings” policy group will have both the policies shown as enabled:

Google Update
As mentioned before, this is a separate policy template that is provided by Google. If imported correctly, the policy template should be included as “Google Update” under “Google”, as shown below:

Flash is a built-in plugin installed with Chrome, and the latest version of Flash will be installed once the browser is updated.
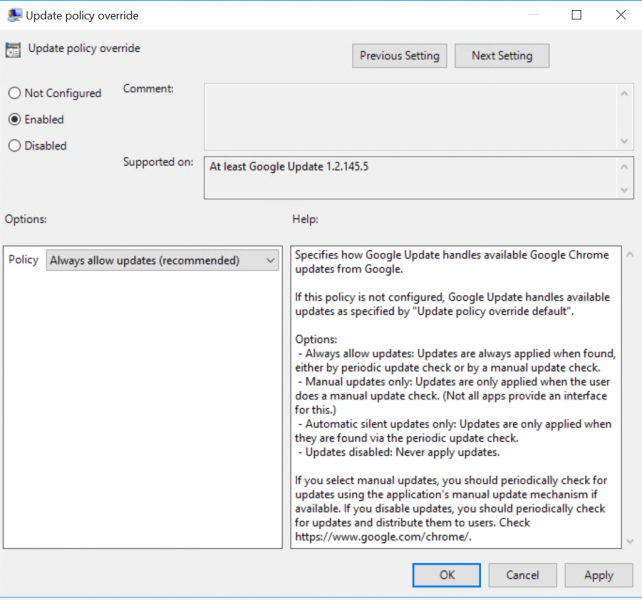
Google Chrome Update Policy Override
This policy specifies how Google Update handles available Google Chrome updates from Google, it is recommended to have this enabled and configured to “Always allow updates”. This will enable automatic updates every 24 hours as configured in the policy above, and allow manual updates should the automatic update fail.

Firefox
There are many ways that Flash restrictions can be implemented for Mozilla Firefox depending on the environment that each organisation has.
Although Firefox also has its own policy template that can be imported under “Administrative Templates”, it does not contain policies to restrict the use of Flash and the installation and use of all plugins. Fortunately, Mozilla Firefox’s GitHub repository has included an alternative solution, to create a policies.json file and place it in a newly created “distributions” directory where the EXE is located.
The simplest option is to use a logon script, that will add the JSON file containing Firefox configurations to the “distribution” folder within the Firefox installation directory. Another solution is to write an installation script to include the JSON file as part of the installation and then deploy this to the workstations within the estate using a central management system such as Microsoft’s System Centre Configuration Manager (SCCM). The examples of the policies in JSON shown below configure the built-in policies within the Firefox Browser (Kaply, 2019).
JSON Policies
FlashPlugin
The following policy sets the behaviour of Flash on the specified domains, as well as the default behaviour (Kaply, 2019). This allows system administrators to whitelist websites that can run Flash, set the default Flash value on whether to block all websites to run Flash or allow any website to run Flash. The system administrator can then set the “Lock” value to choose whether or not users can access the Flash setting.
The recommended configuration is to:
- List all trusted websites in the “Allow” list, within double quotes separated by commas.
- Do not change the block and default value.
- Set the value of “Locked” to true to prevent users from changing the FlashPlugin setting.
{
"policies": {
"FlashPlugin": {
"Allow": ["https://example.org/"], /* Sites on the allow list do not override Flash being completely disabled */
"Block": ["https://example.edu/"],
"Default": [true|false], /* If this is set to true, Flash is always enabled. If it is set to false, Flash is never enabled */
"Locked": [true|false]
}
}
}
Logon Scripts
Logon scripts are used to assign tasks when a user logs on to a particular computer, and are used to carry out operating system commands, set system environment variables, and call other scripts or execute programs (Petri, 2009).
A logon script can be written in any Windows scripting language, including batch and visual basic, and can be assigned using two ways:
- The first is via the profile tab of the user properties dialog in the Active Directory User and Computers (ADUC).
- The second is done via Group Policy Objects (GPO), which can be assigned to an Active Directory site, Active Directory domain or an Organisational Unit (OU).
Both of these can be used to include the JSON file in the current installation folder of Firefox when the user logs in.
More information on these two methods can be found in the following links:
https://www.petri.com/setting-up-logon-script-through-gpo-windows-server-2008
The below shows an example of a simple batch script that creates a folder “distribution” and copies the JSON file from a network share to that folder.
@ECHO OFF Cd "C:\Program Files\Mozilla Firefox\" Mkdir distribution XCOPY "\\<SHARE LOCATION>\Firefox\distribution\policies.json" distribution /Y EXIT
More information regarding the recommendations and other optional policies to include in the JSON file can be found from the following link:
https://github.com/mozilla/policy-templates/blob/master/README.md
Disable Flash in Internet Explorer
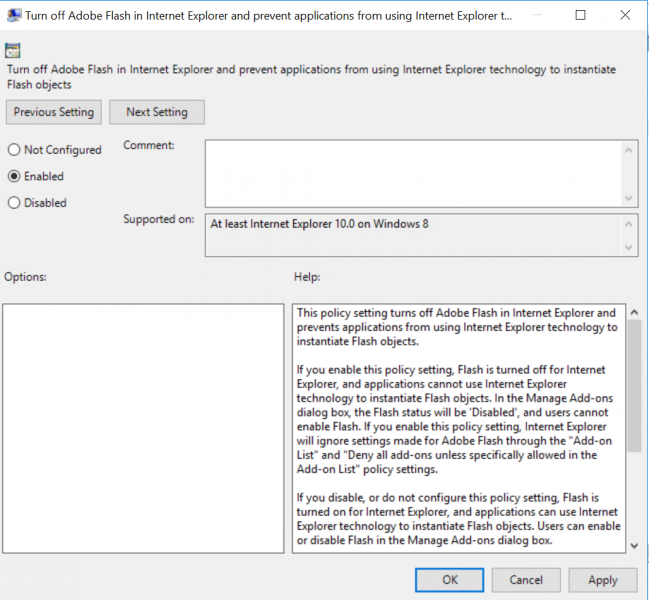
After Chrome and Firefox have been configured, Flash will need to be disabled on Internet Explorer across all workstations. This can be configured by navigating to Computer Configuration -> Policies -> Windows Components -> Internet Explorer -> Security Features -> Add-on Management and then enabling the setting “Turn off Adobe Flash in Internet Explorer and prevent applications from using Internet Explorer technology to instantiate”.

Disable Flash in Edge
Please note that this solution can only be configured manually on Windows 10 Enterprise or Pro machines. It is recommended that this method is implemented as part of a build image prior to deployment.
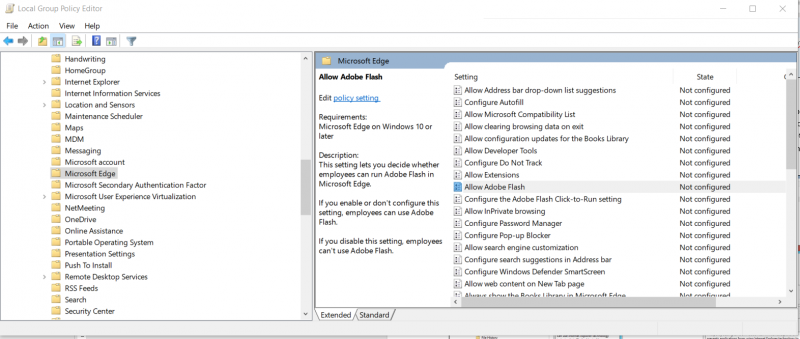
Open up the Local Group Policy Editor as an administrator on the Windows 10 machine. Navigate to Computer Configuration -> Administrative Templates -> Windows Components -> Microsoft Edge and scroll down to the policy “Allow Adobe Flash”, as shown in the image below:

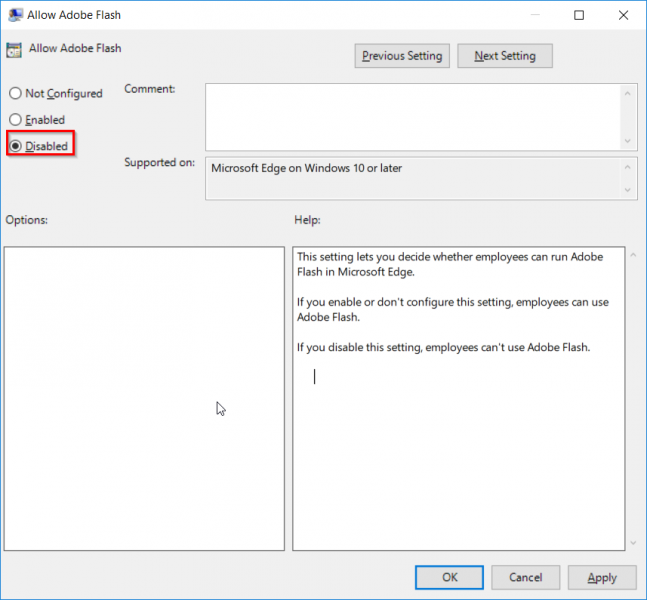
Right click on the policy and select “Edit”. Select “Disabled” and click “OK” to apply the setting. As mentioned in the description, this configuration will prevent users from using Adobe Flash in Edge.

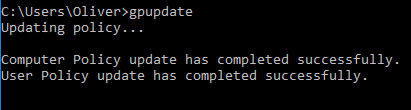
Once this is configured, open up a command prompt as an administrator and run the command gpupdate. This will update both Computer Policies and User Policies, as shown below:

Now to test that this policy is configured correctly, open up Edge and click on the button on the top right with 3 dots, and select “Settings”.
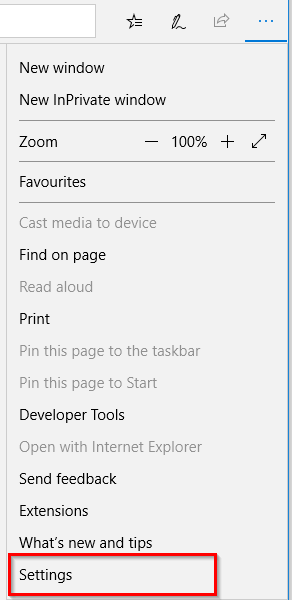

Scroll to the bottom and select “View advanced settings”
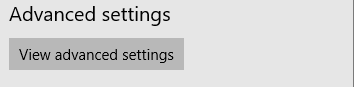

A message will appear at the top, indicating that some settings are restricted by the organisation and the setting for “Use Adobe Flash Player” will be greyed out, thus preventing users from changing this setting.
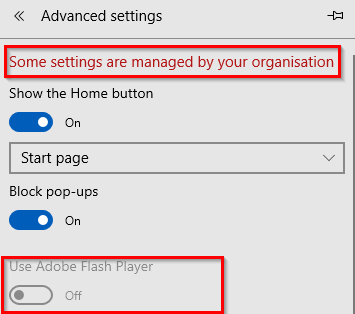

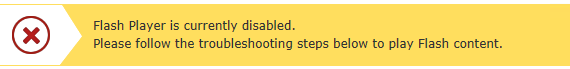
Browse to https://helpx.adobe.com/flash-player/kb/flash-player-issues-windows-10-edge.html and click on the button “Test Flash Player”. This will show a warning that Flash player is disabled.


On the other hand, if Flash player is enabled, the following Flash content would run.


Conclusion
Hopefully, this blog has given plenty of insight into how to minimize the risks of using Flash, and restricting the sites to which a plugin enabled browser has access.
References
Adobe Corporate Communications, 2017. Flash & The Future of Interactive Content. [Online]
Available at: https://theblog.adobe.com/adobe-flash-update/
[Accessed April 2019]
Adobe, 2019. Adobe Flash Player. [Online]
Available at: https://helpx.adobe.com/uk/security.html#flashplayer
[Accessed April 2019].
Aims Digital, 2018. Critical Steps for A Successful Flash to HTML5 migration Of Your eLearning Courses. [Online]
Available at: https://medium.com/@aimsdigitallms/critical-steps-for-a-successful-flash-to-html5-migration-of-your-elearning-courses-b99f7d88f8a9
[Accessed 16 April 2019].
CVE Details, 2019. Adobe Flash Player Security Vulnerabilities. [Online]
Available at: https://www.cvedetails.com/vulnerability-list/vendor_id-53/product_id-6761/Adobe-Flash-Player.html
GPO Edit, 2017. Allow Flash In Chrome For Specific Website Via GPO. [Online]
Available at: https://www.gpoedit.com/2017/10/allow-flash-specific-website-via-gpo/
[Accessed 3 April 2019].
Kaply, M., 2019. Mozilla Policy Templates. [Online]
Available at: https://github.com/mozilla/policy-templates/blob/master/README.md
[Accessed 4 April 2019].
Margaret Rouse, 2014. address space layout randomization (ASLR). [Online]
Available at: https://searchsecurity.techtarget.com/definition/address-space-layout-randomization-ASLR
[Accessed 12 April 2019].
Petri, D., 2009. Setting up a Logon Script through Active Directory Users and Computers in Windows Server 2008. [Online]
Available at: https://www.petri.com/setting-up-logon-script-through-active-directory-users-computers-windows-server-2008
[Accessed 4 April 2019].
Petri, D., 2009. Setting up a Logon Script through Active Directory Users and Computers in Windows Server 2008. [Online]
Available at: https://www.petri.com/setting-up-logon-script-through-active-directory-users-computers-windows-server-2008
[Accessed 12 April 2019].
Smith, C., 2017. Adobe Flash Replacement. [Online]
Available at: https://www.agitraining.com/adobe/creative-cloud-training/adobe-flash-replacement
The Chromium Projects, 2019. Policy List. [Online]
Available at: https://www.chromium.org/administrators/policy-list-3#DefaultPluginsSetting
[Accessed 3 April 2019].
Like what you see? Share with a friend.




