Recently I spent a little time trying to integrate Hydra (THC-Hydra) into Nessus. I thought to share this so you might save a bit of time if you are trying to achieve the same thing. I have been told by the Nessus support team that if you have installed the latest version of Nessus, which at the time of writing is 6.2.1, it is also advised to use a version of Hydra prior to 8.1 as well.
As the Hydra command line format changed in version 7.5 at the moment Nessus 6.2.1 does not support Hydra 8.1 or 7.5. Tenable recommend using Hydra version 7.3 for now. So I downloaded that version and installed it on the machine when my Nessus was running:
# wget https://www.thc.org/releases/hydra-7.3.tar.gz # unzip hydra-7.3 # cd hydra-7.3 # ./configure # checkinstall
Now if everything went well you should have hydra 7.3 installed:
# hydra Hydra v7.3 (c)2012 by van Hauser/THC & David Maciejak - for legal purposes only [...]
As a side note for those who are not familiar with checkinstall command, it does the same thing of “make install” but a bit better. It creates a deb package which is very useful when you want to uninstall it. As Hydra doesn’t come with the option “make uninstall” it might be useful in the future if you want to uninstall the current version of Hydra and install the most recent one.
Now if you open Nessus you should be able to see the Brute Force section with new options, as shown below, where you can upload the usernames and passwords files:
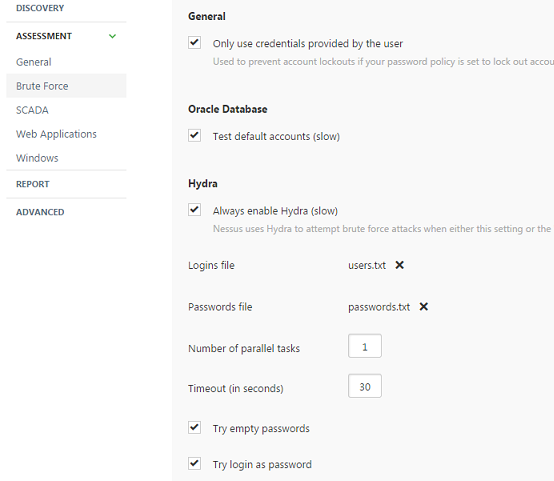

Bear in mind that even if you have those options, it does not necessary mean that the Hydra module is perfectly integrating with Nessus. When I installed Hydra 8.1, Nessus showed those new options but when I ran a test case against one of my SSH servers, Nessus didn’t flag the credentials that I passed into the usernames and passwords files, even though Nessus logs showed that the Hydra SSH NASL plugin ran successfully. So I recommend verifying and testing everything before moving to production.
An example of an issue flagged by Nessus as a result of a successful word dictionary attack is shown below:
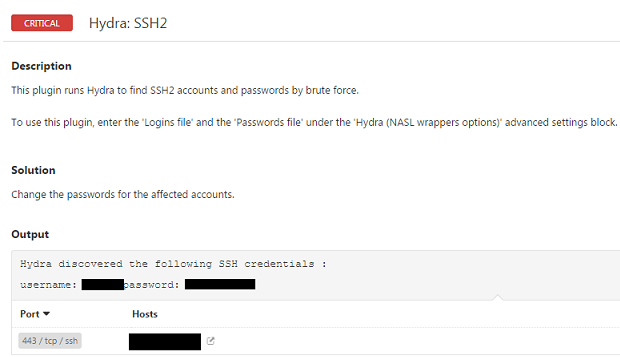

We use manual checks for likely passwords on penetration tests at Dionach, but it’s always good to have a little help from a scanner for the more obvious default passwords.
