During a recent engagement I was asked to perform a penetration test of a Citrix environment. One particular requirement of this test was to see whether I could transfer files back and forth between my local computer and the remote environment.
The easiest way to transfer data was through their web proxy. Although it implemented some sort of web filtering, Internet access was allowed. I encrypted a document in a zip file and then uploaded it to a web server controlled by Dionach. This allowed me to bypass the filters and accomplish the goal.
However, the client requested if it was possible to achieve the same result but not using Internet Explorer. I explained them that another way was via Outlook. By attaching the encrypted document in an email it was possible to transfer the file to an attacker’s email address.
Not entirely convinced, the client asked me if there was another method in case within Citrix environment Internet access was completely denied.
I started messing around with Citrix preferences and settings. When you connect to the remote machine via Citrix on top of the Desktop Viewer there some configurations settings, but unfortunately it didn’t let me get very far.

Copy and Paste was disabled and I could not drag and drop files. However, eventually I came up with this solution which allowed me to transfer files quite easily via USB redirection. The steps are:
1) Connect a USB drive to the local machine.

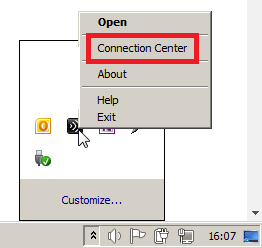
2) Open “Connection Center” by right-clinking the Citrix icon in the Notification Area on bottom right of the Windows taskbar.

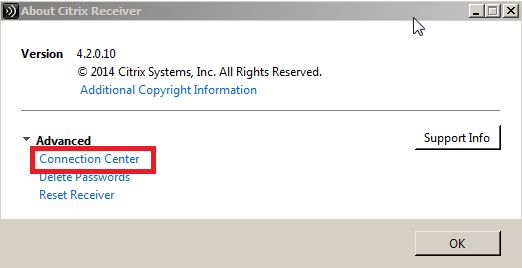
3) Click “Connection Center” under Advanced tab.

4) Inside “Connection Center” expands all the options. In my case I had the option to launch an instance of Microsoft OneNote 2010 by double clicking on the icon.
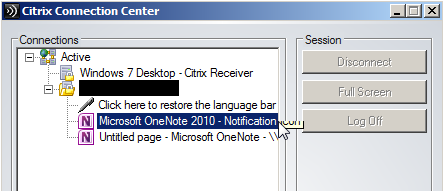

5) Inside Microsoft OneNote, go to “open” and then “browse”.
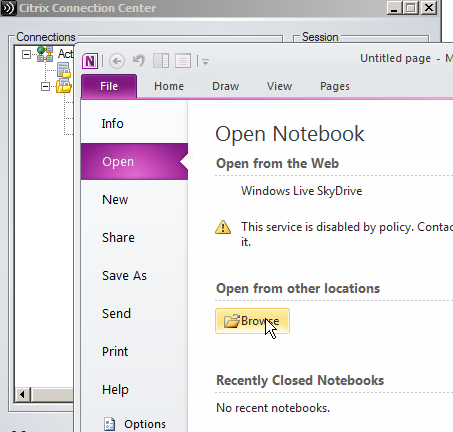

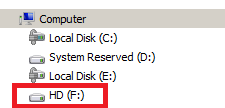
6) At this stage it is now possible to access the local USB drive within the Citrix environment.
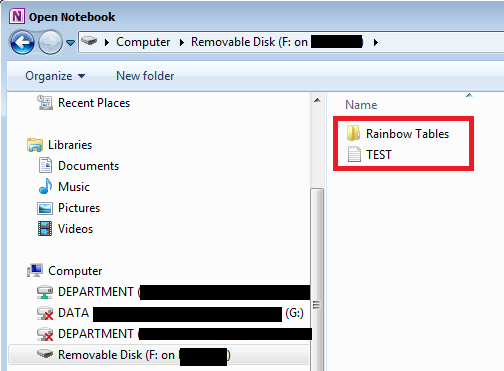

7) Using copy and paste functionality, I copied the TEST.txt file to the Desktop of the Citrix environment.
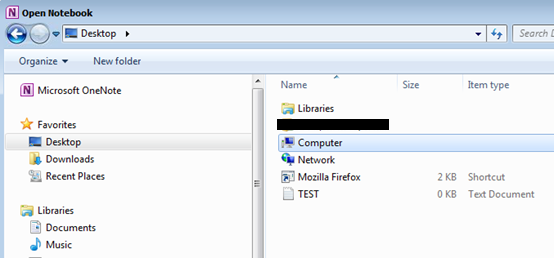

8) The TEST.txt file is therefore available on the Desktop of the Citrix environment.
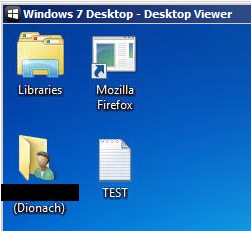

9) The same process can be used to copy files from the Citrix environment to the local computer.
In this particular case Citrix allowed me to map local USB drives, highlighting a poor configuration of Citrix. The following articles provide further information on how to enable and disable USB redirection.
https://support.citrix.com/article/CTX137939
https://support.citrix.com/proddocs/topic/xenapp-xendesktop-76/xad-hdx-usb-cdm.html
Dionach recommend that Citrix environments are regularly tested in order to find vulnerabilities which can be used by attackers such as a rogue employee. As it happened in this case, by breaking out of the Citrix environment, it allowed the Dionach consultant to have a foothold in the internal network and eventually to compromise the entire domain.
