Most antivirus systems today use signature-based detection in order to identify given binaries as malware. Malware authors adapting to this with anti-forensic tooling has lead to the use of behavioural and heuristic analysis in order to detect and classify malware types. It is possible to identify malware types exclusively from analysing the network behavioural patterns that these malwares engage in.
There also exist models for using other behavioural indicators, such as API interaction patterns, to classify malware type. However, as most malware needs to utilise networked communication in order to operate effectively, network data extraction is a rich datasource with regards to identifying malware type. Some malware types and their respective network behavioural signatures are discussed in this blog post.
Worms
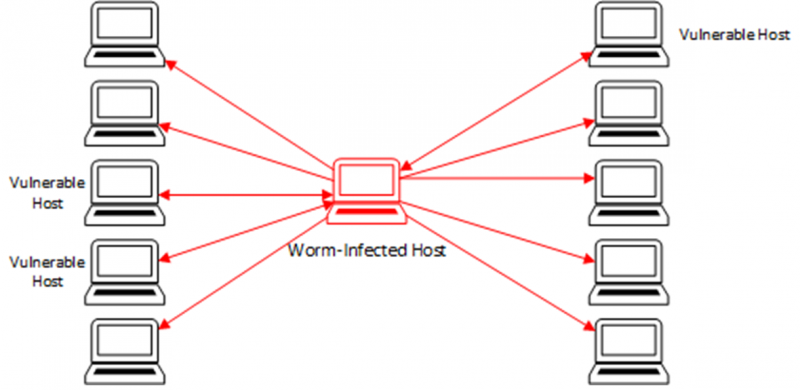
Worms are self-propagating malware with noisy network traffic. Perhaps the most distinctive network signature is that of malware that can be classified as a worm. This network signature is, by virtue of the network traffic necessary for it’s operation, a lot of scanning activity on a small range of ports, across a large number of external hosts. The worm may also attempt to reconnoitre the local network ranges to ascertain whether it is able to move laterally on the local network and compromise further machines. This scanning activity may be followed by deploying payloads to target hosts that appear to have vulnerable configurations. This is quite a noisy method of propagation, and as such leaves a lot of network forensic evidence.
Worms have not been a common malware class in recent years, as compared to their heyday in the late 90s and early 2000s with worms such as SQL Slammer, Iloveyou (Melissa) or Code Red. However, they have experienced a resurgence in popularity since 2016, as their method of propagation is highly effective for distribution of ransomware, wiper or cryptojacking payloads. Wiper malware is malware that is designed to wipe target systems of all data and cryptojacking malware is malware that is designed to enable the hijacking of compute cycles in order to illicitly mine cryptocurrency.

Droppers
Droppers are executables that download larger malware payloads, with highly asymmetric network traffic. Droppers are less of an independent malware variant than they are a meta-type of malware, as a stage in the deployment of other more complex malware types. Droppers are the initial executable loaded onto a target computer for the purpose of downloading the full malware payload. To this end they function as a catalyst for other malware classes to achieve their goal.
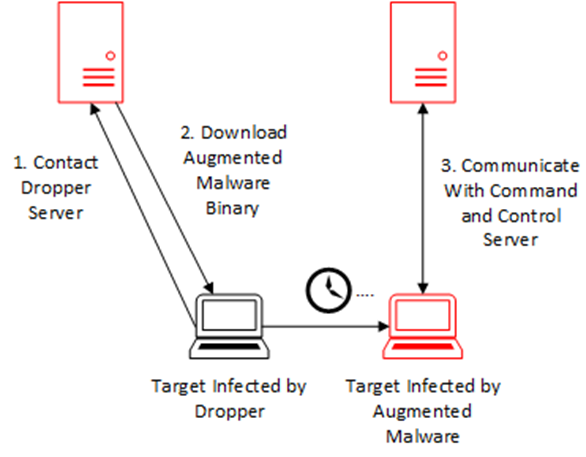

The primary characteristic of the network signature of a dropper is the asymmetry of the volume of data sent as compared to that received. As the sole purpose of dropper binaries is to download and install the more substantial latter stages of the malware’s killchain, it will download a significant amount more data than it uploads.
Ransomware
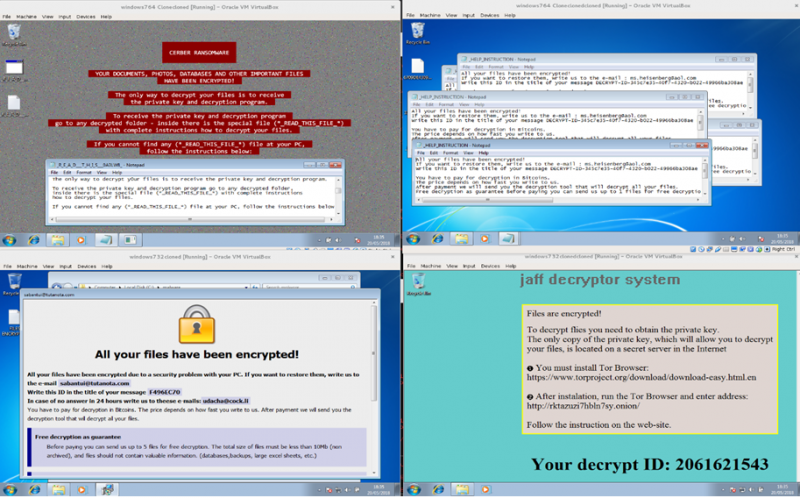
Ransomware is malware that self-propagates and encrypts user data, with a network signature very similar to that of worms, depending on type, with subtle differences. Ransomware is a prevalent form of malware, with variants such as Petya and Wannacry making news headlines across the world. In terms of its memory fingerprint on affected devices, it is highly visible, as it encrypts the entire hard drive or significant amounts of files, then alerts the user to its presence. However, the network signature is somewhat more subtle, and less obvious than other malware classes.
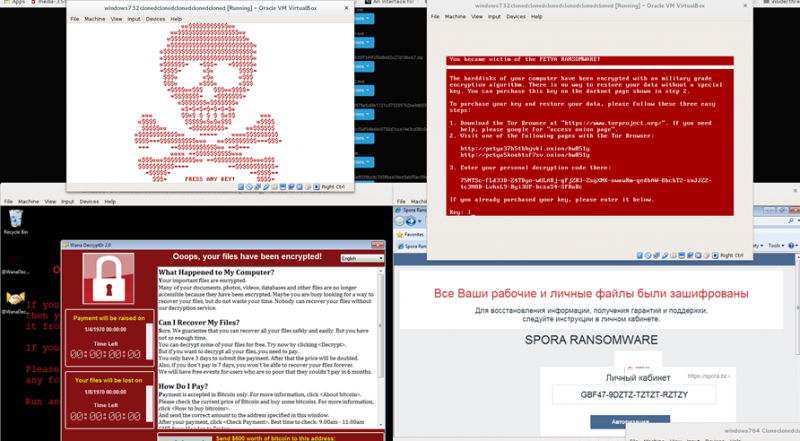

The network signature is typified by a “worm-like” propagation methodology, alongside intermittent communication with command and control servers, for the purpose of key distribution. The reason for a worm-like propagation mechanism is the linear correlation between the amount of hosts infected and the amount of profit a given ransomware campaign is able to achieve. As it is not an operational priority for the virus to remain stealthy during transmission, the only real obfuscation methodology is that of obscuring the command and control server architecture to prevent takedowns by law enforcement. This can be achieved through the use of bulletproof hosting, fast-flux command and control servers, or routing communications through the Tor network.

Cryptominers
Malware which utilises the target’s computational resources in order to mine cryptocurrency for the profit of the criminal operators is known as crypto-mining malware or cryptojacking. Cryptominers are a malware classification that has grown as a percentage of the active malware corpus in the first two quarters of 2018. Unlike ransomware, their modus operandi when infecting systems is to remain unnoticed by the system owner in order to continue utilising their computational resources for as long as possible. Typically the currency being mined will be Monero (XMR), due to its mining algorithm’s superior performance on CPUs.
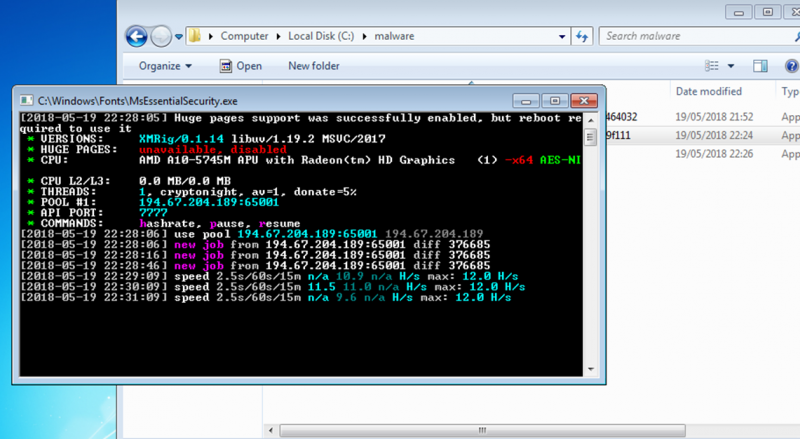

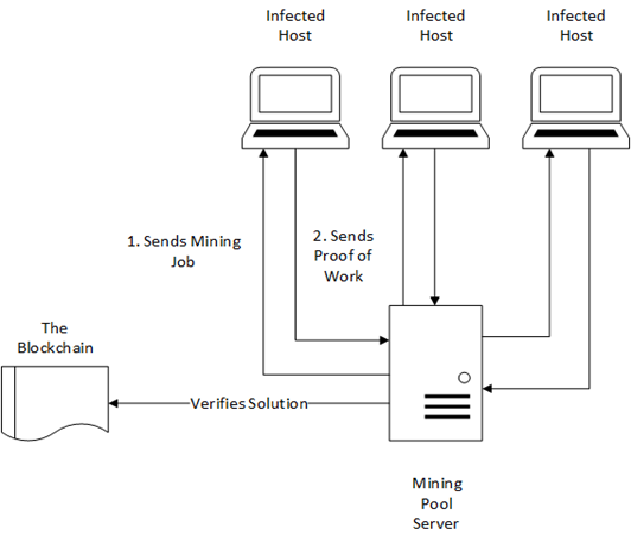
However cryptojacking malware has one key behaviour which can be identified within its network footprint. During the initial execution of the malware it will broadcast a number of join requests to a “mining pool”. This is a group of computers which will collaborate with each other to mine the chosen cryptocurrency. The necessity of the malware connecting to the mining pool that has been established, is for the purpose of collaborating with other computers within the pool to attain the cryptocurrency that is being mined. During the initial execution of the malware it will broadcast join requests to this pool.

Additionally, research by Adguard has shown that many sites, both legitimate and illegitimate are using certain JavaScript libraries to surreptitiously utilise their visitors’ computational power to mine cryptocurrency. These are easily identified on the targeted devices themselves due to the massive increase in use of computational resources by the web browser. The network signature of these miners is also quite easily identified, as it is HTTP traffic, transmitted to a small range of commonly-blacklisted domains, that can be compared versus a blacklist. Although these network traces are not as noticable as the massive increase in use of computational resources by a given browser resultant from in-browser cryptojacking.
Remote Access Trojans
Remote Access Trojans are a variant of malware that enables the remote command and control of a victim’s computer. This may be a targeted attack, or victims may form part of a network of ‘botted’ computers that form a botnet, a botnet being a network of infected computers. This is a long-standing malware class, that has its origins in malicious software from the 1990’s such as SubSeven and Poison-Ivy which enabled remote command and control of targets.
Remote access tools have evolved substantially since then, with malware such as ZeuS, Gh0st, Nanocore and Emotet having far more subtle and intricate deployment and control architectures. These deployment architectures enable persistence on computers, a wide range of infected hosts and the prevention of fraud detection algorithm triggering. Due to the increased profitability of digital financial fraud, subtlety and remaining stealthy during execution are important. This increased profitability is due to the move towards online banking and payment methodologies in addition to fierce competition between banking Trojan families.
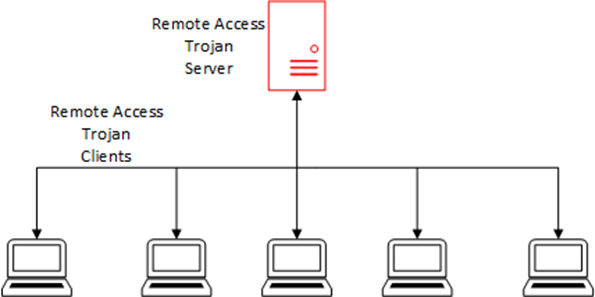

In order for remote access tools to function, they need to maintain effective and continual communications via their command and control infrastructure. A simplified model of this architecture is shown above, though in reality there will be shifting intermediary proxy layers between the botmaster and the bots. This leaves a distinctive network trace. This network trace can be identified by continued communication to a number of IP addresses. They may also be using bulletproof hosting and switch rapidly via fast-flux or double fast-flux domain switching techniques. Bulletproof hosting is server hosting by less than reputable companies who do not comply with law enforcement takedown requests. Fast-Flux technology is covered in another blog post here, on the subject of malware anti-forensics.
Tor
Tor is “The Onion Routing”, which is an anonymity-focused communications protocol, initially developed by the Free Haven project and U.S. Naval Research Laboratory. This protocol, despite a range of innovative and politically conscious purposes, in the context of network forensics of malware, is almost always indicative of malicious activity taking place. The anonymity provisioned by this network enables cybercriminal activities to be conducted with a greater degree of discretion than on the clearnet.
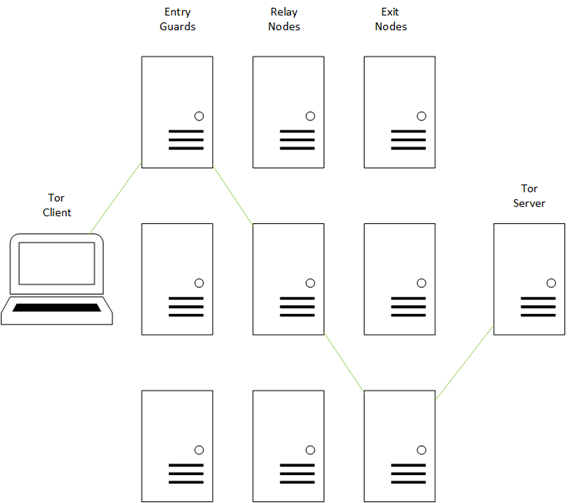

Entry guards are the ‘first hop’ that traffic takes when entering the tor network, then the connection is typically routed through a number of relay nodes. In the transit between these relay nodes, the traffic then exits through exit nodes. After the exit nodes, the tor traffic arrives at its destination, that being a tor server running a ‘hidden service’ or ‘rendevous point’.
Conclusion
Within this blog post there have been a number of malware classes analysed, with their network behavioural indicators illustrated. This has served as an indication of how network behaviour is a necessary part of the operation of modern malware and, as such, may act as a reliable indicator of malware class.
Like what you see? Share with a friend.




